In my previous blogpost I talked about the true random number generator (TRNG) within the Raspberry Pi. Now I am using it for a small online pre-shared key (PSK) generator at https://random.weberlab.de (IPv6-only) that you can use e.g. for site-to-site VPNs. Here are some details how I am reading the binary random data and how I built this small website.
This project is just for fun. I am using a Raspberry Pi 2 B with Raspbian GNU/Linux 9 (stretch), Kernel 4.9.59-v7+. It is accessible via IPv6 only. It consists of two parts: the random generation and the PHP script that reads it.
rng-tools
The hardware random generator is available on all Raspberry Pi models. With root privileges you can read out random data from /dev/hwrng. In order to route the hwrng to /dev/random you must install the rng-tools:
|
1 2 |
sudo apt-get update sudo apt-get install rng-tools |
(Other guides list some more commands to edit the /etc/default/rng-tools file in order to set the hardware device, but I didn’t need that. In my case it was running out of the box without any further configuration.)
Now you can read random data from /dev/random without (!) root privileges such as: (with base64 encoding to have the binary random readable)
|
1 |
head -c 112 /dev/random | base64 -w 30 |
Just for interest you can watch the entropy_avail file which shows the current available entropy. Without the hardware random generator this would immediately decrease and only increase slowly. With the hwrng it stays between 2000-4000 constantly even if you read out random data quite often. You can use the following command to watch the available entropy while refreshing the output every 0.5 seconds:
|
1 |
watch -n 0.5 cat /proc/sys/kernel/random/entropy_avail |
PHP Script
I am using a small PHP script that reads out random data from /dev/random and encodes it with base64 to have only printable characters. I adjusted the length to read out 21 bytes = 168 bits to have 28 chars after the base64 encoding which is a very good starting point for PSKs. That is: The security level is 168 bits for these random data which is quite good!
This is the PHP code snippet:
|
1 2 3 |
<?php print exec("head -c 21 /dev/random | base64"); ?> |
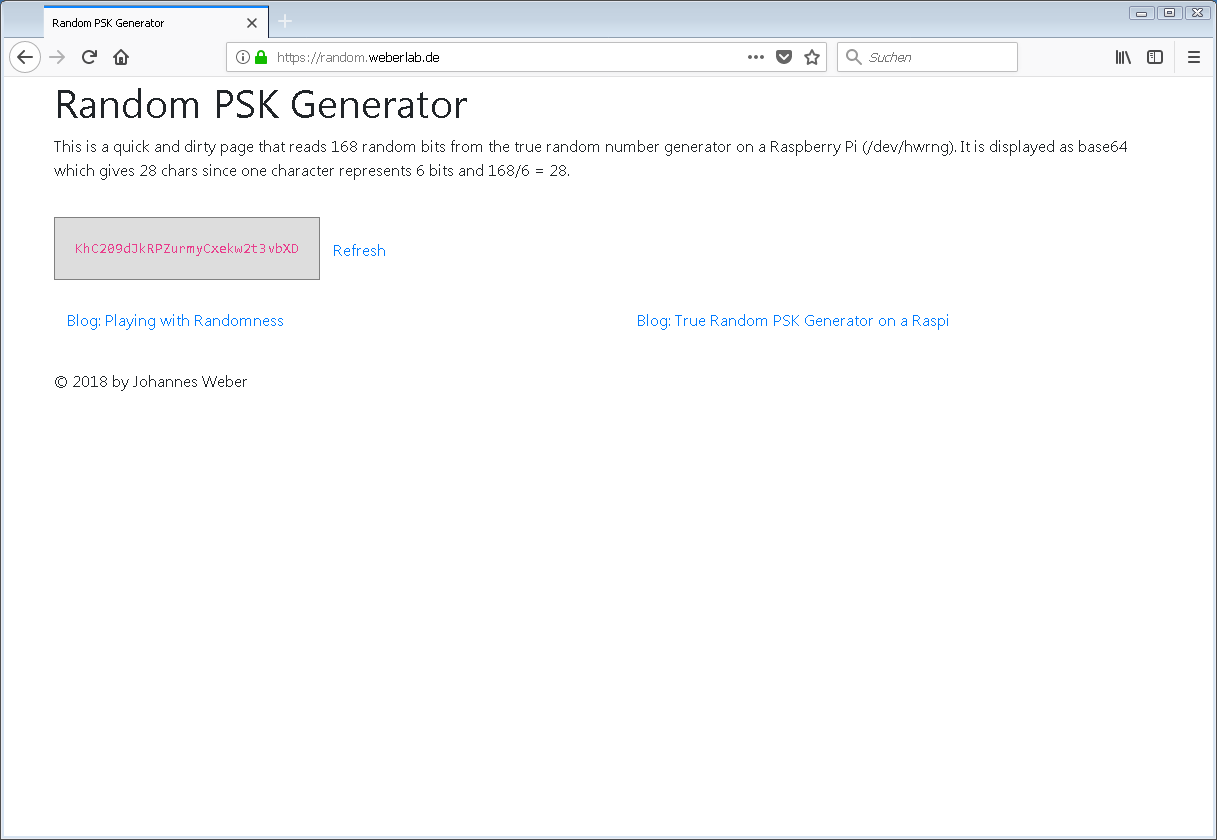
When you look at the page at https://random.weberlab.de you’ll see the quick-and-dirty approach. ;) Give it a try and press F5 for a couple of times – just for fun. Feel free to pick up a random string for your passwords, PSKs, whatever. Note that this servers runs at IPv6-only. If you don’t have IPv6 yet, go and ask your ISP or admin for it! (A last resort would be the usage of an online IPv6 proxy such as http://www.ipv6proxy.net/ to get an idea of the site.) Anyway, this is a screenshot:
And of course I am using only TLS secured https. Thanks to Let’s Encrypt.
Featured image “44742” by Tekniska museet is licensed under CC BY 2.0.

If there is anything I could change about the Linux kernel, it would be the following:
1. Get rid of the blocking /dev/random, and just symlink it to /dev/urandom
2. Remove the misunderstood /proc/sys/kernel/random/entropy_avail file
3. Block reading from /dev/urandom on boot until it’s been sufficiently seeded
Something you might want to be aware of, and may cause you to stop seeding /dev/urandom with the RPi HWRNG:
https://twitter.com/DefuseSec/status/408975222163795969
Basically, this shows that if the HWRNG (like RDRAND or the RPi) knows the state of the CSPRNG, it can manipulate the state, to provide compromised output (IE: a backdoor).
One quick comment- if you wanted https://random.weberlab.de/ to be fully trusted, rather than generating the PSK server-side, and sending it to the page, generate it client-side in JavaScript with window.crypto.getRandomValues(), which uses the browser’s CSPRNG (Chrome and Firefox both fallback to the OS CSPRNG for the data). Then people can be assured that you’re not logging the generated keys with IP addresses. Just a thought.
Hey Aaron. Thanks a lot for your comments. Really appreciate it.
Yes, I would not trust a server-side PSK generation as well. ;) It’s more or less a hobby project to have this TRNG running at the Pi. At least I can use it myself since I really know that I am not logging the keys.
Hello.
Is there really a hardware random number generator installed? Not just a pseudo-random generator?
I am only aware of two methods.
First, the decay of a radioactive element such as strontium 90.
Second, quantum tunneling.
As in this USB stick: https://ubld.it/truerng_v3
Roger Nelson called him, when I emailed Princeton University.
They also use it after the end of “PEAR” in “The Global Consciousness Project”.
But if a Raspberry PI can do the same thing, i don’t need to order such a USB stick.
Such a PI can also be used more universally.
I also need software, and the manufacturer told me they don’t have any software.
Nothing, no demo software, no knowledge of the existence of software from elsewhere, etc.
Because I have no programming knowledge, I need something for finished software to be available.
Or someone writes the few lines of code for the general public.
Maybe I am underestimating the effort, but the stick spits out the random numbers connected via a virtual COM port.
For the beginning, something would be good that shows 50/50 (e.g. as coins, heads or tails, or black / white etc.), and below that also logs how often which result occurred.
E.g. combined with a timer for a measurement over 1, 2, 3 … minutes.
Hey Tobias,
AFAIK there are some more random sources in the real world, such as: https://en.wikipedia.org/wiki/Hardware_random_number_generator#Classical_random_properties
Whether or not the TRNG on the Pi is *really* a *proven* TRNG is not decided by me. ;) I would not recommend it for enterprise security services unless someone has really checked the (open source?) hardware design, and so on. For me, it perfectly fits for playing around with it.
Cheers
Johannes
Hello Tobias
did you succeded with the ” Global Consciousness Project”?
E.g. I m thinking about using the Raspberry as a RNG for experimantaion.
Did you finished such a project?
I want to play with randomness too ;-)
Let me know please.
Thanks
Laco
Hello.
Coincidentally just found here again while googling for help (e.g. volunteer programmers).
I don’t want to participate in the “Global Consciousness Project”.
This is a worldwide network of random generators at mostly universities.
It waits a long time for catastrophes, terrorist attacks, spectacular deaths of celebrities, etc. to detect deviations.
“Ideal” are 9/11, Tsunami 2004, the death of Diana etc…. Those were the big deviations.
The deviations even started to get stronger hours before the events.
This also proves that precognition is reality. So “clairvoyance”.
But in this case purely passive. And the billions of people on earth did not foresee this consciously, of course.
There were also experiments with a True RNG in a classical concert to detect a deviation by the emotions of the audience.
But these are all passive measurements.
We want to measure active influence.
Like at Princeton in the PEAR program.
Instead of individuals on site, it should be many viewers in livestreams on Twitch or YouTube as participants.
And for that, as in Princeton’s PEAR program, it needs at least a 50/50 split.
Like a coin flip, but e.g. 1, 2, 4…. times per second, and over, say, 30, 60, 90, 120 seconds.
In that time, the viewers in the livestream are supposed to focus intensely on the same target.
Here is a description that describes this and possible other functions:
1.
Logging and displaying the 50/50 distribution of a true random generator over adjustable clock and adjustable time period.
Display of raw distribution, percentage and p-value.
E.g. for Raspberry PI and ubld.it “TrueRNG” “V.3” or “Pro” USB stick.
2.
Possible other functions to display the random data.
E.G.:
– An adjustable set of numbers from an adjustable number space with an adjustable number of digits.
With the option of uniqueness of each number.
E.g. to predict lottery numbers.
– Generation of graphical white noise.
Adjustable color depth, color/grayscale/B&W, resolution etc..
As a single image or video (frame rate adjustable).
Display of data rate for choosen video settings.
Optional automatic limitation to an adjustable data rate (of the RNG hardware).
Possibility of saving as a file.
– Generation of acoustic white noise over an adjustable or arbitrarily long period of time.
Adjustable sampling rate and bit depth.
Possibility of saving as a file.
– Generation of date and/or time. Period selectable.
Option for 2, 3, 4… Date determinations with the result of an average value.
– Generation of a geo-coordinate.
The whole earth and adjustable radius (km, miles) around given place.
Option for 2, 3, 4… Location determination with the result of a geographic mean value.
Comparable with “Randonautica”.
– Generation of letters (incl. Ä,Ö,Ü and ß), numbers and the normal special characters (Shift+ key).
Activate and deactivate letters/words, numbers, umlauts, eszett (ß).
Enable and disable other character sets and Unicode.
Adjustment to single letters or only whole words.
For whole words, storable dictionaries.
Comparable with “Ovilus”.
GUI:
Modern interface that displays elements and output data in full screen/window (responsive design) in a large and clear way.
Use of the available space.
No “Win-95 software” look with small menus, Buttons, etc..
More “tablet”-like GUI.
Everything should be clearly visible even on a filmed and streamed monitor.