Similar to my test with Diffie-Hellman group 14 shown here I tested a VPN connection with elliptic curve Diffie-Hellman groups 19 and 20. The considerations why to use these DH groups are listed in the just mentioned post – mainly because of the higher security level they offer. I tested the site-to-site IPsec connections with a Juniper ScreenOS firewall and a Fortinet FortiGate firewall. (Currently, neither Palo Alto Networks nor Cisco ASA support these groups.)
The numbers for the groups are specified in RFC 5114: Additional Diffie-Hellman Groups for Use with IETF Standards. And according to this document on p. 30 (from the “European Network of Excellence in Cryptology”), the bits of security for the elliptic curve groups are the following:
- Group 19 = 256-bit EC = 128 bits of security
- Group 20 = 384-bit EC = 192 bits of security
That is, both groups offer a higher security level than the Diffie-Hellman groups 14 (103 bits) or 5 (89 bits). When using group 20 in IPsec phase 2 (PFS) with AES-256, the security level of the whole VPN connection is really 192 bit!
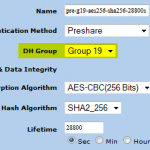
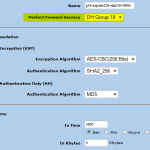
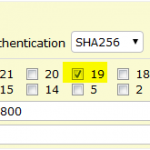
Test Group 19
The config changes for my test VPN between the SSG and the FortiGate were trivial. These are the proposals I am using now:
The site-to-site IPsec tunnel came up without any problems. The SSG reveals the correct crypto algorithms used for this VPN with the following CLI commands:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 |
fd-wv-fw01-> get ike cookies IKEv1 SA -- Active: 9, Dead: 0, Total 9 80102f/0003, 172.16.1.6:500->172.16.1.1:500, PRESHR/grp19/AES256/SHA2-256, xchg(5) (fd-wv-fw04/grp-1/usr-1) resent-tmr 322 lifetime 28800 lt-recv 28800 nxt_rekey 28119 cert-expire 0 responder, err cnt 0, send dir 1, cond 0xc0 nat-traversal map not available ike heartbeat : disabled ike heartbeat last rcv time: 0 ike heartbeat last snd time: 0 XAUTH status: 0 DPD seq local 0, peer 548098 fd-wv-fw01-> fd-wv-fw01-> fd-wv-fw01-> get sa id 0x000000e index 7, name fd-wv-fw04, peer gateway ip 172.16.1.6. vsys auto key. tunnel if binding node, tunnel mode, policy id in:<-1> out:<-1> vpngrp:<-1>. sa_list_nxt:<-1>. tunnel id 14, peer id 7, NSRP Local. site-to-site. Local interface is ethernet0/6 <172.16.1.1>. esp, group 19, a256 encryption, s256 authentication autokey, IN active, OUT active monitor<1>, latency: -1, availability: 100 DF bit: clear app_sa_flags: 0x24001a7 proxy id: local 0.0.0.0/0.0.0.0, remote 0.0.0.0/0.0.0.0, proto 0, port 0/0 ike activity timestamp: -1118626869 DSCP-mark : disabled nat-traversal map not available incoming: SPI f41f7e9f, flag 00004000, tunnel info 4000000e, pipeline life 3600 sec, 2847 remain, 0 kb, 0 bytes remain anti-replay on, last 0x5e0, window 0xffffffff, idle timeout value <0>, idled 0 seconds next pak sequence number: 0x0 bytes/paks:14333168/321762; sw bytes/paks:14333168/321762 outgoing: SPI c97b1226, flag 00000000, tunnel info 4000000e, pipeline life 3600 sec, 2847 remain, 0 kb, 0 bytes remain anti-replay on, last 0x0, window 0x0, idle timeout value <0>, idled 0 seconds next pak sequence number: 0x5e0 bytes/paks:14141960/319910; sw bytes/paks:14141960/319910 |
However, I have not found a command on the FortiGate to display the Diffie-Hellman group that is used for a certain VPN. Does anyone know?!?
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 |
fd-wv-fw04 # get vpn ike gateway fd-wv-fw01 vd: root/0 name: fd-wv-fw01 version: 1 interface: wan1 6 addr: 172.16.1.6:500 -> 172.16.1.1:500 created: 1869s ago IKE SA created: 1/2 established: 1/2 time: 220/9230/18240 ms IPsec SA created: 1/14 established: 1/1 time: 200/200/200 ms id/spi: 20472 3441a7d55dce8550/73e8df93e0546c26 direction: initiator status: established 1869-1851s ago = 18240ms proposal: aes-256-sha256 key: 24f1972f370db1aa-83d5bfccd6c8332f-86d89c6ad33dd4ef-c1b3a19711119192 lifetime/rekey: 28800/26648 DPD sent/recv: 00085ddd/00000000 fd-wv-fw04 # fd-wv-fw04 # fd-wv-fw04 # get vpn ipsec tunnel name fd-wv-fw01 gateway name: 'fd-wv-fw01' type: route-based local-gateway: 172.16.1.6:0 (static) remote-gateway: 172.16.1.1:0 (static) mode: ike-v1 interface: 'wan1' (6) rx packets: 3588 bytes: 590220 errors: 0 tx packets: 3589 bytes: 328150 errors: 12 dpd: enabled/negotiated idle: 5000ms retry: 3 count: 0 selectors name: 'blubb' auto-negotiate: disable mode: tunnel src: 0:0.0.0.0/0.0.0.0:0 dst: 0:0.0.0.0/0.0.0.0:0 SA lifetime/rekey: 3600/1721 mtu: 1438 tx-esp-seq: e00 replay: enabled inbound spi: c97b1226 enc: aes 57ea27c4a01879ffe650c020cf32b7d4ad27fe92bb55522784880afa20e6c57c auth: sha256 88301accbbb19a968174a943d8ab8deec844ed1f97a2db8bef0204e94c213d08 outbound spi: f41f7e9f enc: aes 3d4e8405915d14f953b2fd943d7e4eb2411b5ff92fe5ce089c420b04bc65f5a6 auth: sha256 1644e58d3e736b922bbce2a28368cf452f7ee7097a21607c70952a435fd67ebc NPU acceleration: encryption(outbound) decryption(inbound) fd-wv-fw04 # fd-wv-fw04 # fd-wv-fw04 # diagnose vpn tunnel list name fd-wv-fw01 list ipsec tunnel by names in vd 0 ------------------------------------------------------ name=fd-wv-fw01 ver=1 serial=2 172.16.1.6:0->172.16.1.1:0 lgwy=static tun=intf mode=auto bound_if=6 proxyid_num=1 child_num=0 refcnt=9 ilast=0 olast=0 stat: rxp=4100 txp=4101 rxb=655840 txb=393614 dpd: mode=active on=1 idle=5000ms retry=3 count=0 seqno=548360 natt: mode=none draft=0 interval=0 remote_port=0 proxyid=blubb proto=0 sa=1 ref=2 serial=3 src: 0:0.0.0.0/0.0.0.0:0 dst: 0:0.0.0.0/0.0.0.0:0 SA: ref=7 options=0000000e type=00 soft=0 mtu=1438 expire=1499/0B replaywin=1024 seqno=1000 life: type=01 bytes=0/0 timeout=3572/3600 dec: spi=c97b1226 esp=aes key=32 57ea27c4a01879ffe650c020cf32b7d4ad27fe92bb55522784880afa20e6c57c ah=sha256 key=32 88301accbbb19a968174a943d8ab8deec844ed1f97a2db8bef0204e94c213d08 enc: spi=f41f7e9f esp=aes key=32 3d4e8405915d14f953b2fd943d7e4eb2411b5ff92fe5ce089c420b04bc65f5a6 ah=sha256 key=32 1644e58d3e736b922bbce2a28368cf452f7ee7097a21607c70952a435fd67ebc dec:pkts/bytes=4097/655556, enc:pkts/bytes=4101/393966 npu_flag=03 npu_rgwy=172.16.1.1 npu_lgwy=172.16.1.6 npu_selid=9 |
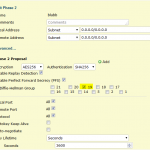
Test Group 20
And, of course, very similar for group 20 (while still only the SSG shows the active DH groups in its command line output):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 |
fd-wv-fw01-> get ike cookies IKEv1 SA -- Active: 9, Dead: 0, Total 9 80102f/0003, 172.16.1.6:500->172.16.1.1:500, PRESHR/grp20/AES256/SHA2-256, xchg(5) (fd-wv-fw04/grp-1/usr-1) resent-tmr 322 lifetime 28800 lt-recv 28800 nxt_rekey 28743 cert-expire 0 responder, err cnt 0, send dir 1, cond 0xc0 nat-traversal map not available ike heartbeat : disabled ike heartbeat last rcv time: 0 ike heartbeat last snd time: 0 XAUTH status: 0 DPD seq local 0, peer 551543 fd-wv-fw01-> fd-wv-fw01-> fd-wv-fw01-> get sa id 0x000000e index 7, name fd-wv-fw04, peer gateway ip 172.16.1.6. vsys auto key. tunnel if binding node, tunnel mode, policy id in:<-1> out:<-1> vpngrp:<-1>. sa_list_nxt:<-1>. tunnel id 14, peer id 7, NSRP Local. site-to-site. Local interface is ethernet0/6 <172.16.1.1>. esp, group 20, a256 encryption, s256 authentication autokey, IN active, OUT active monitor<1>, latency: -1, availability: 100 DF bit: clear app_sa_flags: 0x24001a7 proxy id: local 0.0.0.0/0.0.0.0, remote 0.0.0.0/0.0.0.0, proto 0, port 0/0 ike activity timestamp: -1099508533 DSCP-mark : disabled nat-traversal map not available incoming: SPI f41f7ed6, flag 00004000, tunnel info 4000000e, pipeline life 3600 sec, 3491 remain, 0 kb, 0 bytes remain anti-replay on, last 0xd9, window 0xffffffff, idle timeout value <0>, idled 0 seconds next pak sequence number: 0x0 bytes/paks:17442652/358913; sw bytes/paks:17442484/358911 outgoing: SPI c97b1237, flag 00000000, tunnel info 4000000e, pipeline life 3600 sec, 3491 remain, 0 kb, 0 bytes remain anti-replay on, last 0x0, window 0x0, idle timeout value <0>, idled 0 seconds next pak sequence number: 0xd9 bytes/paks:17251740/357065; sw bytes/paks:17251740/357065 |
Featured image “A Voice At The End Of The Line” by Jeremy Brooks is licensed under CC BY-NC 2.0.



Hey,
we expect some articles about Ruckus Zonedirector :)
Thanks
However, I have not found a command on the FortiGate to display the Diffie-Hellman group that is used for a certain VPN. Does anyone know?!?
Answer:
This Information can be found in the Output of the following command.
diag debug application ike -1
The Information is in the the proposal Information when the tunnel comes up.
type=DH_GROUP, val=ECP256
So you Need to check this Information in the RFCs.
ECP256 -> DH Group 19