This is a tutorial on how to configure the GlobalProtect Gateway on a Palo Alto firewall in order to connect to it from a Linux computer with vpnc.
Short version: Enable IPsec and X-Auth on the Gateway and define a Group Name and Group Password. With this two values (and the gateway address), add a new VPN profile within vpnc on the Linux machine. Login with the already existing credentials.
Long version with screenshots comes here:
I assume that an already working GlobalProtect configuration is in place. The tested PAN-OS version was 6.0.1.
Configuration Palo Alto
The main step is the activation of IPsec (which is useful for the mere GlobalProtect client, too), and the X-Auth Support on the GlobalProtect Gateway. A group name and group password must be set, just like the VPN-Client settings on a Cisco ASA firewall.
Furthermore, the “from untrust to untrust” security policy must be expanded with at least the application “ciscovpn“. But due to the application dependency warnings after a successful commit on the PA, it is less annoying if “dtls” and all the other dependencies for ciscovpn are allowed, too, though they are not needed. In this way, the commit warnings can be reduced.
That is, I am permitting the following applications for the complete GlobalProtect process, incl. GlobalProtect client, etc.:
Linux: vpnc
I ran a Ubuntu 13.10 with Linux kernel 3.11.0-18 on my test machine.
The following two applications must be installed:
|
1 |
sudo apt-get install vpnc network-manager-vpnc |
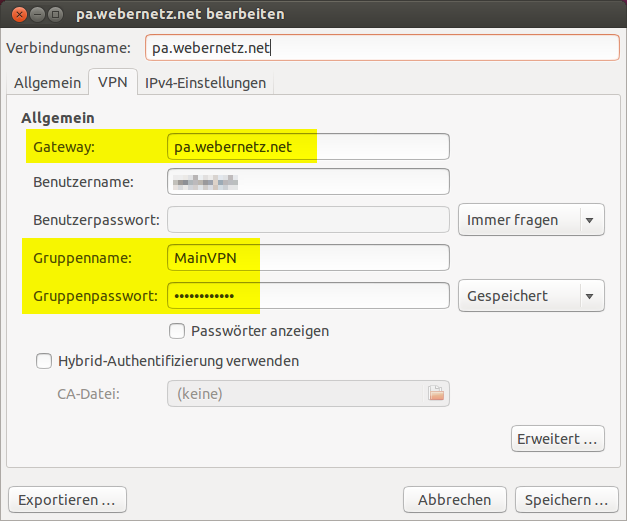
To add a VPN connection, click on the network symbol in the upper right corner: VPN-Connections -> VPN configuration -> Add -> Cisco VPN-Client (vpnc). Give it a name and fill in the gateway name/address, the username and the groupname & -password of the just configured GlobalProtect Gateway (sorry for the German screenshot):
Test
To connect to the VPN endpoint, click on the new VPN profile and type in your account name and password. After a few seconds, the VPN tunnel should be established.
Here are two listings of the IP address of my Linux test machine ( ip a s ) and the routing table ( ip r s ). The first two outputs reveal the values before the VPN tunnel is established:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
weberjoh@JW-NB01-Ubuntu:~$ ip a s 1: lo: <loopback,up,lower_up> mtu 65536 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <no-carrier,broadcast,multicast,up> mtu 1500 qdisc pfifo_fast state DOWN qlen 1000 link/ether 00:15:c5:16:6a:d2 brd ff:ff:ff:ff:ff:ff 3: wlan0: <broadcast,multicast,up,lower_up> mtu 1500 qdisc mq state UP qlen 1000 link/ether 00:13:02:47:49:37 brd ff:ff:ff:ff:ff:ff inet 192.168.1.36/24 brd 192.168.1.255 scope global wlan0 valid_lft forever preferred_lft forever inet6 fe80::213:2ff:fe47:4937/64 scope link valid_lft forever preferred_lft forever weberjoh@JW-NB01-Ubuntu:~$ ip r s default via 192.168.1.1 dev wlan0 proto static 192.168.1.0/24 dev wlan0 proto kernel scope link src 192.168.1.36 metric 9 |
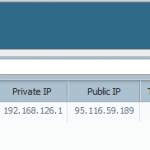
While the following shows the values within the VPN tunnel. A new tun0 interface is present and the default route points to that tun0 interface:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
weberjoh@JW-NB01-Ubuntu:~$ ip a s 1: lo: <loopback,up,lower_up> mtu 65536 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <no-carrier,broadcast,multicast,up> mtu 1500 qdisc pfifo_fast state DOWN qlen 1000 link/ether 00:15:c5:16:6a:d2 brd ff:ff:ff:ff:ff:ff 3: wlan0: <broadcast,multicast,up,lower_up> mtu 1500 qdisc mq state UP qlen 1000 link/ether 00:13:02:47:49:37 brd ff:ff:ff:ff:ff:ff inet 192.168.1.36/24 brd 192.168.1.255 scope global wlan0 valid_lft forever preferred_lft forever inet6 fe80::213:2ff:fe47:4937/64 scope link valid_lft forever preferred_lft forever 4: tun0: <pointopoint,multicast,noarp,up,lower_up> mtu 1412 qdisc pfifo_fast state UNKNOWN qlen 500 link/none inet 192.168.126.1/32 brd 192.168.126.1 scope global tun0 valid_lft forever preferred_lft forever weberjoh@JW-NB01-Ubuntu:~$ ip r s default dev tun0 proto static 80.154.108.228 via 192.168.1.1 dev wlan0 proto static 192.168.1.0/24 dev wlan0 proto kernel scope link src 192.168.1.36 metric 9 |
And by the way: the DNS server in /etc/resolv.conf is NOT changed during the VPN connection. Only the search domain (DNS suffix) correspondent to the network settings in the GlobalProtect Gateway is appended.
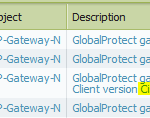
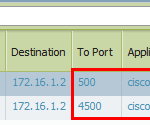
Here are some screenshots of the Palo Alto firewall: The first one shows the Gateway Remote Users with a client of “Linux…”, while the second screenshot shows the System Log with detailed information about the GlobalProtect session: It is recognized as a Cisco VPN Client. After the finished session, the Traffic Log shows at least two sessions with “ciscovpn”, one on port 500 (IKE) and one on port 4500 (ESP inside UDP).
And as always, I am using my http://ip.webernetz.net script to show my current Internet IP address which reveals in this case, that I am surfing through the Palo Alto ISP connection.
Links
- Similar blog post: Connecting to a Palo Alto Network GlobalProtect Gateway from Linux
- Palo Alto: Split Tunneling for VPNC Client on Linux Distributions
Featured image “P8155255 – Wache und brüntender Pinguin.k50” by JojoS7 is licensed under CC BY-NC-ND 2.0.






Hallo Herr Weber,
ich nutze nur noch diese Variante, geht sehr harmonisch.
Als Remote-Desktop nutze “rdesktop”
Übrigens, der gleiche Weg funktioniert auch auf Android –> Smartphone sowie Tablet.
VG
A. Frauenkron
Hello,
I am trying to follow your guide but I keep getting connection failed when I try the upnc connection from ubuntu. also I can see any connection attemps on the palo alto from the IP address im using on ubuntu, it is like it is not trying to connect and the errror I get back is “no response from target” even though I am using the correct gateway IP address
Any idea what could be wrong?
Hi John,
is your GlobalProtect configuration working with the normal GlobalProtect client? So, is your error only from vpnc or in general?
–> A common error is to forget the security policy “from untrust to untrust”. Maybe your Palo Alto is blocking the requests to its own IP address? Please have a look at your traffic log, display the columns “bytes received” and “bytes sent”, and find out whether you have sessions which are blocked or have 0 bytes received.
–> Note that you have to allow “ciscovpn” as an application for this “from untrust to untrust” policy.
–> Otherwise search through the system logs with “( subtype eq globalprotect )”. Maybe you will find some hints there.
hi ,
don’t know if you can help but i followed this excatly and my linux client does connect, but it gets disconnected after 10 seconds or so . i’ve looked at the logs but because the client gets connected the logs are not all that helpfull. I was wondering if you had this issue and what to do about it as i’m going mad . the normal GP client works for win/osx clients.
Thanks
Joe
Hi Joe.
Hm, I am sorry, I did not have this issue as you are describing it. Have you tested any other Linux machines? Are you able to send traffic in both directions through the tunnel, e.g., a ping? Can you sniff on the wire (e.g., with Wireshark) to analyse the packets? Aren’t there any log entries about the disconnection?
So, my question is, how does this affect my current GlobalProtect users? If I enable this, do those users then need the group name and password?
No, they don’t. It is only an addon. No affect for the GlobalProtect app users.
Fantastic! Very glad to hear that.. Many thanks!
Hallo,
ich habe versucht die Cisco AnyConnect App mit der PA zu verbinden (Blackberry BB10) – erfolglos.
Der VPN-Tunnel zwischen dem Windows-Client und der PA läuft tadellos.
Nun habe ich die Erweiterung nach Eurer Anleitung gemacht
Es gibt einfach zu viele Parameter bei der App zum einstellen.
Z.B. Gateway-Typ (Cisco AnyConnect, Juniper IPsec, Microsoft IKEv2 usw..)
Könnt Ihr eine App empfehlen, über die man einen VPN-Tunnel aufbauen kann,
ohne GlobalProtect nutzen zu müssen?
Hi Marco,
ich kenne mich leider nicht mit Blackberry aus. Das “AnyConnect” VPN von Cisco wird definitiv nicht funktionieren, da es ein reines SSL-VPN von Cisco ist. Du brauchst schon einen IPsec Client. Vielleicht kann der Blackberry so etwas nativ, ähnlich zu Android oder iPhone (wie ich es in anderen Posts beschrieben haben).
Rein vom Namen her könntest du auch das “Juniper IPsec” mal probieren, weil Palo Alto mit Juniper ja in gewisser Weise verwandt ist.
Hallo Johannes,
ich werde es mal testen und berichten.
Danke, ciao Marco
Thank you.
Hallo,
seit dem Update der PA auf 7.1 funktioniert IPSec leider nicht mehr.
Ist da schon was bekannt, ggf. ein globales Problem mit der 7.1 OS?
Die Einstellungen unter GlobalPrtotect Gateway Configuration –> Tunnel Settings –> Agent (bei 7.1) sind identisch mit GlobalProtect Gateway –> Tunnel Settings –> Client Configuration (bei 7.0).
Muss eventuell nur einmal das Group Password neu eingegeben werden?
Gruß
Günter
Hi,
VPNC does not work when Multi Factor Authentication (Radius OTP) is enabled. Do know of a fix or work around for this?
Thanks!
James
Sorry James, but I have not worked with vpnc and Radius OTP on the Palo so far.
Hello, I found Palo Alto global protect doesn’t add the configured “access routes” (in Client configuration ->Network Setting ) to the linux client so all traffic is forced to pass by the VPN tunnel (tun0) as you said in this howto. In windows/MacOS clients the routes all perfectly added to the client machine as long the client is “preconfigured”.
I know I can add the routes manually (or in vpnc’s script) but I want to be configured on Palo Alto to avoid noob people to make mistakes or modify their linux systems. Is this possible?
I found myself the answer with “split connection” configuration adding the routes on vpnc “routes table” and “use this connection for resources on its network”.
This way you can use the VPN only for desired networks but you must define any network on the VPN you want to acces by tun0. Is called split tunneling for vpnc.
More info:
https://live.paloaltonetworks.com/t5/Configuration-Articles/Split-Tunneling-for-VPNC-Client-on-Linux-Distributions/ta-p/57244
I hope it will help some other people to configure linux VPN with Palo Alto’s VPN SSL.
My workplace uses Global Protect. I have been connecting from Ubuntu at home, setting up the client side much as you show here. Now they are adding 2FA. I do not have access to the server side so I can’t say exactly how they are doing that. The standard Ubuntu “Configure VPN” doesn’t seem to have any setting related to 2FA. The IT department seems to expect that after my username/password are sent, a text message will be sent to my cell phone with a code. I have no idea where I would enter this code. They only deal with Windows/Mac and can’t help with any kind of Linux. Do you have any information on how 2FA works with GP and how a Ubuntu VPN client might be coerced to work with it?
Sorry Jeff, but I cannot help you. :( I have not used it with 2FA.
You would put the passcode after your password with a comma.
password,passcode
This is if they are using Duo Auth Proxy with Global Protect.
guys if my companion didnt have group user and group password i can’t connect cause in global protect in windows form input just give, 3 input colom username, password, and portal
Thank you very much. Works great!!