This time I configured a static S2S VPN between a Palo Alto firewall and a Cisco IOS router. Here comes the tutorial:
I am not using a virtual interface (VTI) on the Cisco router in this scenario, but the classical policy-based VPN solution. That is, no route entry is needed on the Cisco machine. However, the Palo Alto implements all VPNs with tunnel interfaces. Hence, a route to the tunnel and Proxy IDs must be configured. (I also wrote a guide for a route-based VPN between a Cisco router and a Palo Alto firewall here.)
In my test lab I am running a PA-200 with PAN-OS 6.0.3. The Cisco router is an old Cisco 2621 with IOS 12.3(26) and image “c2600-ik9o3s3-mz.123-26.bin”.
Laboratory
The following figure depicts my test laboratory:
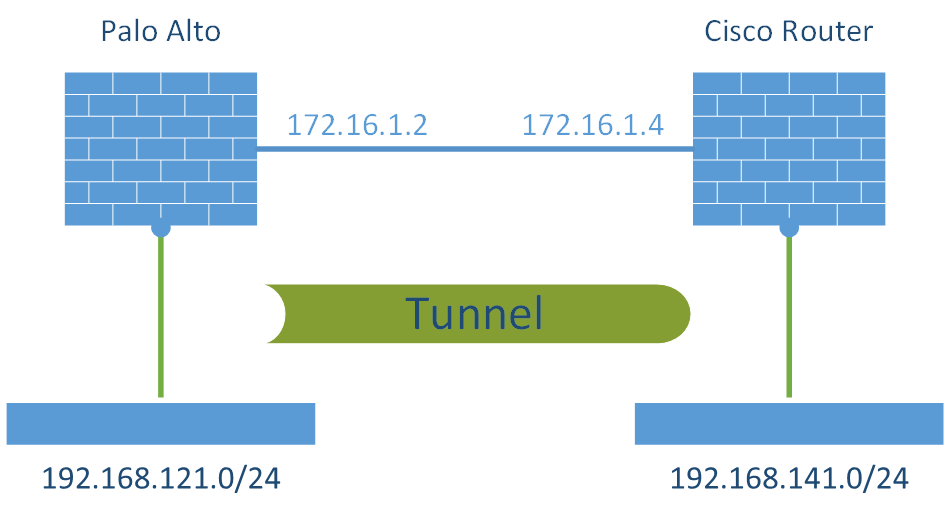
Palo Alto
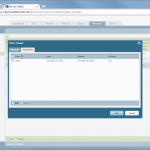
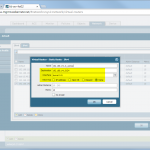
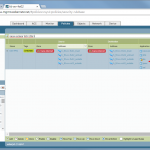
The configuration steps for the Palo Alto Networks firewall are the following:
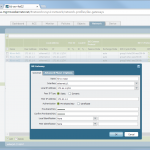
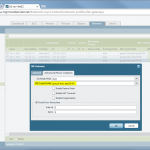
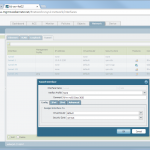
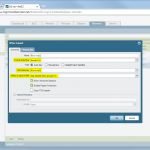
- IKE and IPSec Crypto profiles, e.g., aes256, sha1, pfs group 5, lifetime 8h/1h.
- IKE Gateway with the pre-shared key and the corresponding IKE Crypto Profile. The “Identification” fields are not needed.
- Tunnel Interface within a virtual router (e.g., “default”) and a security zone (e.g., “vpn-s2s”). The interface does not need an IP address.
- IPSec Tunnel: Tying all together: tunnel interface, IKE gateway, IPSec crypto profile. Furthermore, the Proxy IDs (= protected networks) are set here.
- Static route to the destination network through the tunnel interface (without next hop address).
- Policy from untrust to untrust with the applications “ike”, “ipsec”, and “ciscovpn” allowed.
- Policies from trust zones to the zone in which the tunnel interface resides.
Here are my configuration screenshots:
Cisco Router
The Cisco router, configured through the CLI, needs the following lines:
- crypto isakmp appropriate to the “IKE Crypto” on the PA
- crypto isakmp key with the pre-shared key
- crypto ipsec appriopriate to the “IPSec Crypto” on the PA
- access-list which defines the protected networks, corresponding to the “Proxy IDs”
- crypto map with the transform-set, peer, pfs group, and access-list
- crypto map applied to the outside interface
- (Note: No route entry is needed since this VPN is a policy-based VPN which makes its routing decision based on the access-list.)
Here is the bunch of my configuration commands:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
! crypto isakmp policy 10 encr aes 256 authentication pre-share group 5 lifetime 28800 ! crypto isakmp key 3WU99OhGqpPRIhjNm2eBeBG6hQbLQ5 address 172.16.1.2 ! crypto ipsec transform-set aes256-sha esp-aes 256 esp-sha-hmac ! crypto map map01 1 ipsec-isakmp set peer 172.16.1.2 set transform-set aes256-sha set pfs group5 match address acl-vpn-PA ! interface FastEthernet0/0 crypto map map01 ! ip access-list extended acl-vpn-PA permit ip 192.168.141.0 0.0.0.255 192.168.121.0 0.0.0.255 ! |
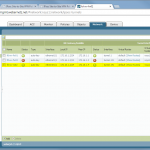
Monitoring
After a successful establishment of the tunnel, the PA shows green bubbles in its IPSec Tunnels overview. The Session Browser reveals active sessions for ike or ciscovpn and ipsec-esp. However, I noticed that after these sessions are gone, only the ike sessions are in my traffic log, while the ipsec sessions are not correct according to the listed traffic bytes. Hm. Has anyone else recognized a similar behaviour?
The Cisco router can be queried with the subsequent commands:
- show crypto isakmp sa detail
- show crypto ipsec sa
- show crypto map
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 |
fd-wv-ro02#show crypto isakmp sa detail Codes: C - IKE configuration mode, D - Dead Peer Detection K - Keepalives, N - NAT-traversal X - IKE Extended Authentication psk - Preshared key, rsig - RSA signature renc - RSA encryption C-id Local Remote I-VRF Encr Hash Auth DH Lifetime Cap. 509 172.16.1.4 172.16.1.2 aes sha psk 5 01:48:09 ------------------------------------------------------------------------------- fd-wv-ro02#show crypto ipsec sa interface: FastEthernet0/0 Crypto map tag: map01, local addr. 172.16.1.4 protected vrf: local ident (addr/mask/prot/port): (192.168.141.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (192.168.121.0/255.255.255.0/0/0) current_peer: 172.16.1.2:500 PERMIT, flags={origin_is_acl,} #pkts encaps: 42122, #pkts encrypt: 42122, #pkts digest 42122 #pkts decaps: 47189, #pkts decrypt: 47189, #pkts verify 47189 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 2, #recv errors 0 local crypto endpt.: 172.16.1.4, remote crypto endpt.: 172.16.1.2 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0 current outbound spi: C0F1609E inbound esp sas: spi: 0x81DF870F(2178909967) transform: esp-256-aes esp-sha-hmac , in use settings ={Tunnel, } slot: 0, conn id: 2080, flow_id: 81, crypto map: map01 sa timing: remaining key lifetime (k/sec): (4516253/1975) IV size: 16 bytes replay detection support: Y inbound ah sas: inbound pcp sas: outbound esp sas: spi: 0xC0F1609E(3237044382) transform: esp-256-aes esp-sha-hmac , in use settings ={Tunnel, } slot: 0, conn id: 2081, flow_id: 82, crypto map: map01 sa timing: remaining key lifetime (k/sec): (4516252/1973) IV size: 16 bytes replay detection support: Y outbound ah sas: outbound pcp sas: ------------------------------------------------------------------------------- fd-wv-ro02#show crypto map Crypto Map "map01" 1 ipsec-isakmp Peer = 172.16.1.2 Extended IP access list acl-vpn-PA access-list acl-vpn-PA permit ip 192.168.141.0 0.0.0.255 192.168.121.0 0.0.0.255 Current peer: 172.16.1.2 Security association lifetime: 4608000 kilobytes/3600 seconds PFS (Y/N): Y DH group: group5 Transform sets={ aes256-sha, } Interfaces using crypto map map01: FastEthernet0/0 |
And one more time: Since the Cisco Router decides its forwarding decisions for VPNs on the policy (ACL) and NOT on route entries, the routing table does NOT show any of my site-to-site remote networks, but only the connected and static configured routes:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
fd-wv-ro02#show ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is 172.16.1.1 to network 0.0.0.0 S 192.168.120.0/24 [1/0] via 172.16.1.2 S 192.168.125.0/24 [1/0] via 172.16.1.2 172.16.0.0/24 is subnetted, 1 subnets C 172.16.1.0 is directly connected, FastEthernet0/0 C 192.168.140.0/24 is directly connected, FastEthernet0/1.140 C 192.168.141.0/24 is directly connected, FastEthernet0/1.141 S* 0.0.0.0/0 [1/0] via 172.16.1.1 |
Links
Similar information about this tunnel can be found here:


What if you have to make 4 policies on the Cisco Router? Do you create 4 tunnels on Palo Alto, or only the proxy id
You mean if you have 4 ACL entries on the Cisco router? Then you have to set up these 4 networks in the Proxy ID section. You do NOT need to create 4 IPsec tunnels.
Thank you so much, and yes I meant 4 ACL or policies on a Juniper Firewall
“And one more time: Since the Cisco Router decides its forwarding decisions for VPNs on the policy (ACL) and NOT on route entries, the routing table does NOT show any of my site-to-site remote networks, but only the connected and static configured routes”
The ACL defines what traffic should be encrypted when it is being routed. However, you will NEED to have a route for your remote destinations. The routing decision is done first. Yes, you do not have the routes explicitly configured. You have a static route with a next hop given. This next hop is reachable out of Fa0/0. Traffic for your remote network will be routed out of Fa0/0 and since this interface has the crypto map applied and now the traffic does match the ACL it will be encrypted.
Forwarding decision is done based on the routing table. What is being encrypted in decided by the ACL.
Can you please show me the example of palo alto to palo alto IPsec?
Sorry, but I am not showing these “vendor A to vendor A” cases. Please read the official Palo Alto documentation where it is explained in detail.
Hi,
I’m not able to establish the vpn connection. I followed the instructions except for the ip addressing part. Not sure what’s the issue. I’m using GNS3 to do the testing. any advice on what to check?
Cheers
Hi Dong,
sorry, I cannot help you. There are MANY potential problems when it comes to IPsec with different vendors. Furthermore, I don’t know how exactly the IPsec implementation is build in GNS3.
Try to debug as much as possible on both sides…
what if instead you had another cisco router behind the palo that wanted to initiate a tunnel with the cisco router on the other side? the palo would be nating traffic to the cisco router…
You mean:
Router <<-->> Palo <<-->> Router
while the VPN is terminated on both routers? Then it’s straightforward, since the Palo only acts as another router than can (but must not) do NAT.