Since my last blogposts covered many 6in4 IPv6 tunnel setups (1, 2, 3) I took a packet capture of some tunneled IPv6 sessions to get an idea how these packets look like on the wire. Feel free to download this small pcap and to have a look at it by yourself.
A couple of spontaneous challenges from the pcap round things up. ;)
At first, this is the pcap. Zipped with 7z, 19.5 Kbyte:
Setup
Two different tunnel endpoints were involved, both with tunnels from Hurricane Electric and its tunnel broker:
- 193.24.227.10, a Juniper SSG 140, tunneling to 216.66.86.114 for IPv6 prefix 2001:470:6d:a1::/64
- 193.24.227.12, a Cisco router, tunneling to 216.66.80.30 for IPv6 prefixes 2001:470:1F0B:1024::/64 and 2001:470:765B::/48
There are some IPv4 packets left within the trace intentionally, just to have some for reference. Within the trace you’ll find tunneled IPv6 connections with the following protocols:
- Ping aka ICMPv6 echo-request
- DNS via UDP
- DNS via TCP
- NTP
- HTTP
- HTTPS aka TLS
- Syslog
IP Protocol 41
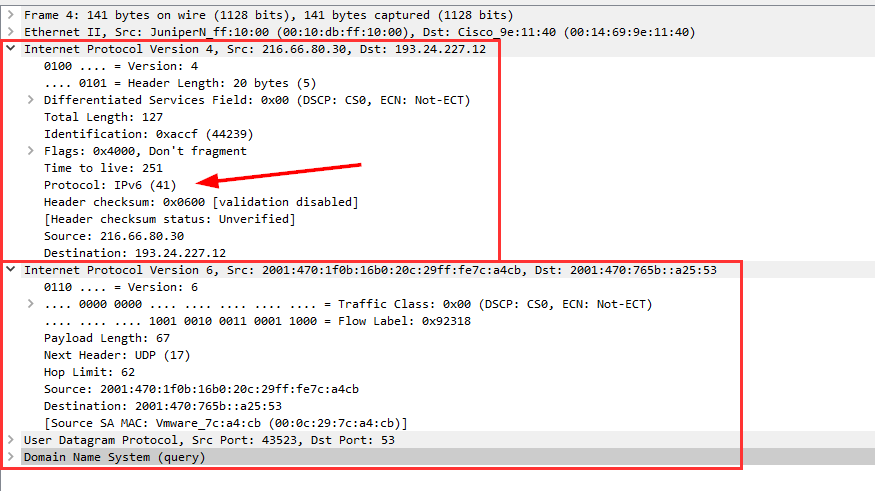
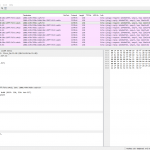
Basically, every IPv6 packet is encapsulated in IPv4, using the IP protocol number 41. This is *not* UDP or TCP, but its own protocol. Ref: IANA – Assigned Internet Protocol Numbers. Looking at it with Wireshark reveals the outer IPv4 packet with “Protocol: IPv6 (41)”, as well as the inner IPv6 packet with its actual payload:
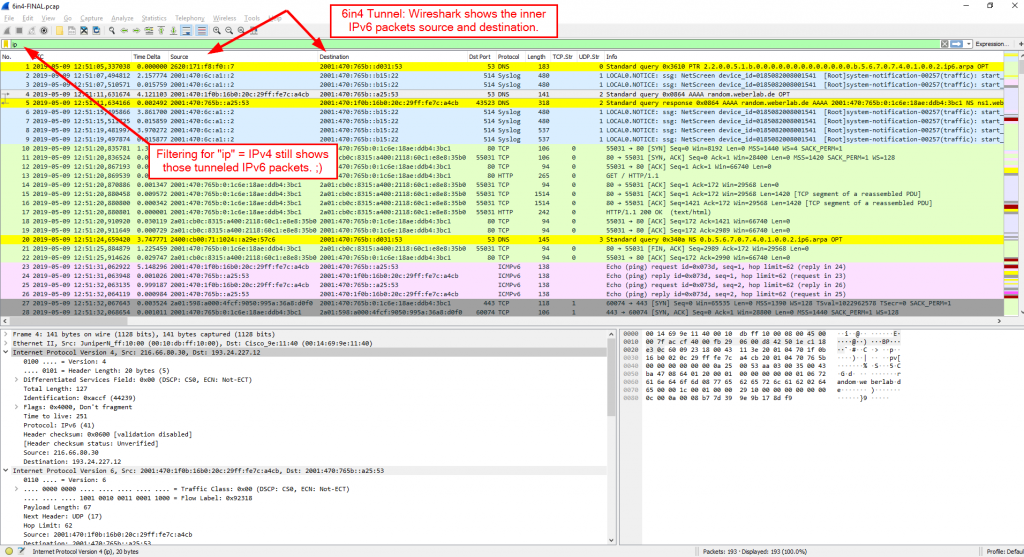
Note that Wireshark displays the IPv6 source and destination address in the packet list and NOT the IPv4 ones. This can be confusing, especially when using display filters such as “ip”. Normally this should show ONLY IPv4 packets, but since those tunneled IPv6 packets are within IPv4, they are still present:
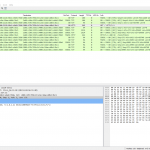
You can filter for some of those mentioned layer 7 protocols such as DNS, NTP, or ICMPv6:
TCP stream 0 shows an HTTP session, TCP stream 1 an HTTPS one:
Spontaneous Challenges
While preparing some screenshots for this post, I came across some ideas for a packet challenge. Just for fun, as always. However, they are not related to those 6in4 packets, but quite generic. Please comment below for the answers!
- What’s the serial number of the Juniper SSG 140?
- What reference time source is used on the stratum 1 NTP server?
- Which operating system sent the ping?
- Which server (vhost) was accessed in TCP stream 4?
- How many authoritative DNS answers were sent from my lab?
- What are the authoritative name servers?
- Which DNSSEC algorithm is weberlab.de using?
- Which DNS client sent a cookie? What’s its value?
- What’s the first HTML line from the answer in TCP stream 2?
- How many different server TLS certificates are in the trace?
- What are the subject alternative names of the 1st certificate in TCP stream 5?
Have fun! ;)
Featured image “Charli Blake” by Thomas Hawk is licensed under CC BY-NC 2.0.


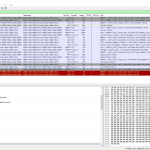
Hi Johannes, as promised, here are my findings/answers to your questions that I previously sent to you by e-mail. Cheers, Sake
1) What’s the serial number of the Juniper SSG 140?
0185082008001541
2) What reference time source is used on the stratum 1 NTP server?
Reference ID: Unidentified reference source ‘PZF’
3) Which operating system sent the ping?
ICMPv6: Not windows, probably Linux
– not “a…w” as payload, but binary 0..255
– wrong IPv6 hop limit (62, so started at 64, not 128)
ICMP: Not windows, probably Linux
– not 32 bytes of payload, but 8 bytes
– wrong IPv6 hop limit (234, so started at 255, not 128)
4) Which server (vhost) was accessed in TCP stream 4?
random.weberlab.de (both in SNI and in certificate)
5) How many authoritative DNS answers were sent from my lab?
3
(use the filter : dns.flags.response == 1 && dns.count.auth_rr> 0)
6) What are the authoritative name servers?
ns1.weberdns.de
ns2.weberdns.de
7) Which DNSSEC algorithm is weberlab.de using?
Algorithm: RSA/SHA-512 (10)
8) Which DNS client sent a cookie? What’s its value?
Source: 2001:470:1f0b:16b0:20c:29ff:fe7c:a4cb
Client Cookie: b77d399e9b178df9
9) What’s the first HTML line from the answer in TCP stream 2?
10) How many different server TLS certificates are in the trace?
Only one
11) What are the subject alternative names of the 1st certificate in TCP stream 5?
dNSName: ip-only.webernetz.net
dNSName: ip.webernetz.net
dNSName: ipv4-only.webernetz.net
dNSName: ipv4.webernetz.net
dNSName: ipv6-only.webernetz.net
dNSName: ipv6.webernetz.net
dNSName: random.weberlab.de
Wow, Sake, thank you very much for your efforts in solving the challenges. ;) You were the first to answer all questions! Congrats!
You can configure additional columns to show the outer IPs as well. I have a GIF explaining how to do that in this blog post (in the “Field Occurence” section): https://blog.packet-foo.com/2018/08/wireshark-column-setup-deepdive/