Here comes a small lab consisting of three Cisco routers in which I used OSPFv3 for IPv6 with IPsec authentication. I am listing the configuration commands and some show commands. Furthermore, I am publishing a pcapng file so that you can have a look at it with Wireshark by yourself.
Laboratory
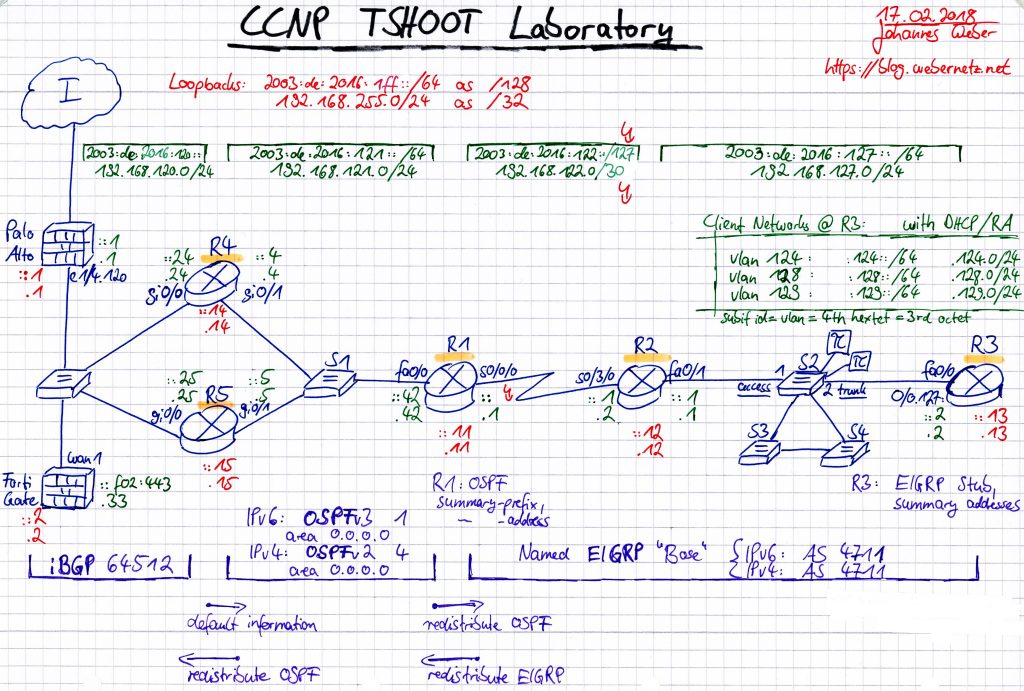
This is the complete lab with OSPFv3 in the middle between R4/R5 and R1:
Some notes about it:
- single backbone area 0.0.0.0
- passive-interface default
- R4 and R5 distributing their default route ::/0
- R1 is redistributing its routes learned from EIGRP, “Type-5 AS External Link States”
- R1 also has a summary-prefix, just to have some variance in the lab. Note the “via Null0, directly connected” route in the show commands section.
- OSPFv3 authentication via IPsec authentication header AH, manually configured on the involved interfaces with “ipv6 ospf authentication ipsec spi 2311 sha1 …”.
- These “type 7 encrypted” stored passphrases can be reverted to its plain text values via password crackers. In my lab I used a randomly generated hex-string of 40 chars with KeePass pattern h{40}.
- This automatically adds an IPv6 access-list. Refer to the show commands below where you can also see the appropriate IPsec crypto security associations.
- In the trace file you’ll see the following three link-local IPv6 addresses:
- R4: FE80::215:62FF:FE6A:FEF1
- R5: FE80::225:45FF:FE60:17C1
- R1: FE80::21E:7AFF:FE79:3F10
The configuration commands for all three routers are:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 |
! ########## R4 ########## ! interface Loopback0 ipv6 address 2003:DE:2016:1FF::14/128 ipv6 ospf 1 area 0.0.0.0 ! interface GigabitEthernet0/0 description Uplink zu Dell-Switch Port 20 ipv6 address 2003:DE:2016:120::24/64 ipv6 nd ra suppress all ipv6 ospf 1 area 0.0.0.0 ! interface GigabitEthernet0/1 description Downlink zu S1 Port 1 ipv6 address 2003:DE:2016:121::4/64 ipv6 nd ra suppress all ipv6 ospf 1 area 0.0.0.0 ipv6 ospf authentication ipsec spi 2311 sha1 7 0255250E2D505E7819185A3B214442522A5C727F76786A61744054415158070B0007712C544C300C0A ! ipv6 router ospf 1 router-id 192.168.255.14 default-information originate passive-interface default no passive-interface GigabitEthernet0/1 ! ! ! ########## R5 ########## ! interface Loopback0 ipv6 address 2003:DE:2016:1FF::15/128 ipv6 ospf 1 area 0.0.0.0 ! interface GigabitEthernet0/0 description Uplink zu Dell-Switch Port 20 ipv6 address 2003:DE:2016:120::25/64 ipv6 nd ra suppress all ipv6 ospf 1 area 0.0.0.0 ! interface GigabitEthernet0/1 description Downlink zu S1 Port 2 ipv6 address 2003:DE:2016:121::5/64 ipv6 nd ra suppress all ipv6 ospf 1 area 0.0.0.0 ipv6 ospf authentication ipsec spi 2311 sha1 7 014027517D5D5756741A1D2B3D56474B2D545C7E7974716763714050445A5004010C767659573E430B ! ipv6 router ospf 1 router-id 192.168.255.15 default-information originate passive-interface default no passive-interface GigabitEthernet0/1 ! ! ! ########## R1 ########## ! interface Loopback0 ipv6 address 2003:DE:2016:1FF::11/128 ipv6 ospf 1 area 0.0.0.0 ! interface FastEthernet0/0 description Uplink zu S1 Port 24 ipv6 address 2003:DE:2016:121::42/64 ipv6 nd ra suppress all ipv6 ospf 1 area 0.0.0.0 ipv6 ospf authentication ipsec spi 2311 sha1 7 091F6F5C3F53464B5E5A57080F77786A137A4B53445358020F0B00035C5A4944010C72710501725E09 ! interface Serial0/0/0 description Downlink zu R2 Port s0/3/0 bandwidth 8000 ipv6 address 2003:DE:2016:122::/127 ipv6 nd ra suppress all ipv6 ospf 1 area 0.0.0.0 clock rate 8000000 ! ipv6 router ospf 1 router-id 192.168.255.11 summary-prefix 2003:DE:2016:1FF::12/127 passive-interface default no passive-interface FastEthernet0/0 redistribute eigrp 4711 include-connected ! |
pcapng
Here you can download the zipped pcapng file. I captured in on R1 port fa0/0:
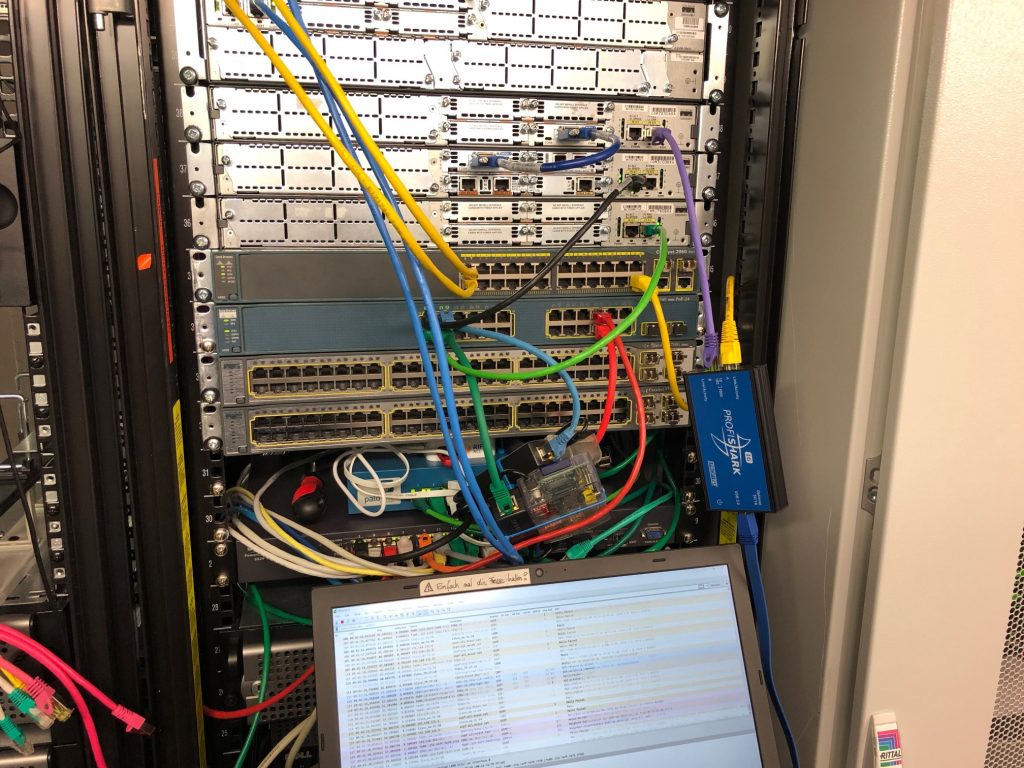
One more time I used my ProfiShark 1G for capturing the packets between the routers. See it hanging around in my lab. ;)
Analyzing the dump file with Wireshark you can see for example:
- The IPv6 Authentication Header. Note the “Next Header” field in the former packet, that is: the IPv6 header lists “Authentication Header” as the next header, while the authentication header lists “OSPF” as its next header.
- Note that OSPF is not a TCP/UDP protocol but an own IP protocol with number 89, refer to the IANA Protocol Numbers.
- OSPF update packet with LSA type 9 intra-area prefix LSA or
- OSPF update packet with LSA type 5 AS-external LSA advertising the default route ::/0 from both upstream routers in my lab, R4 and R5.
show
Finally, here are a few (many ;)) show commands from the router R1. Note the “SHA–1 authentication SPI 2311” line at the neighbor, and the automatically generated IPv6 access-list entry and crypto policy:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 |
R1#show ipv6 protocols IPv6 Routing Protocol is "connected" IPv6 Routing Protocol is "ND" IPv6 Routing Protocol is "ospf 1" Interfaces (Area 0.0.0.0): Loopback0 Serial0/0/0 FastEthernet0/0 Redistribution: Redistributing protocol eigrp 4711 include-connected R1# R1# R1#show ipv6 ospf Routing Process "ospfv3 1" with ID 192.168.255.11 Event-log enabled, Maximum number of events: 1000, Mode: cyclic It is an autonomous system boundary router Redistributing External Routes from, eigrp 4711 include-connected Initial SPF schedule delay 5000 msecs Minimum hold time between two consecutive SPFs 10000 msecs Maximum wait time between two consecutive SPFs 10000 msecs Minimum LSA interval 5 secs Minimum LSA arrival 1000 msecs LSA group pacing timer 240 secs Interface flood pacing timer 33 msecs Retransmission pacing timer 66 msecs Number of external LSA 6. Checksum Sum 0x023B2B Number of areas in this router is 1. 1 normal 0 stub 0 nssa Graceful restart helper support enabled Reference bandwidth unit is 100 mbps Area BACKBONE(0.0.0.0) Number of interfaces in this area is 3 SPF algorithm executed 22 times Number of LSA 12. Checksum Sum 0x054085 Number of DCbitless LSA 0 Number of indication LSA 0 Number of DoNotAge LSA 0 Flood list length 0 R1# R1# R1#show ipv6 ospf interface Loopback0 is up, line protocol is up Link Local Address FE80::21E:7AFF:FE79:3F10, Interface ID 10 Area 0.0.0.0, Process ID 1, Instance ID 0, Router ID 192.168.255.11 Network Type LOOPBACK, Cost: 1 Loopback interface is treated as a stub Host Serial0/0/0 is up, line protocol is up Link Local Address FE80::21E:7AFF:FE79:3F10, Interface ID 5 Area 0.0.0.0, Process ID 1, Instance ID 0, Router ID 192.168.255.11 Network Type POINT_TO_POINT, Cost: 12 Transmit Delay is 1 sec, State POINT_TO_POINT Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 No Hellos (Passive interface) Graceful restart helper support enabled Index 1/2/2, flood queue length 0 Next 0x0(0)/0x0(0)/0x0(0) Last flood scan length is 0, maximum is 0 Last flood scan time is 0 msec, maximum is 0 msec Neighbor Count is 0, Adjacent neighbor count is 0 Suppress hello for 0 neighbor(s) FastEthernet0/0 is up, line protocol is up Link Local Address FE80::21E:7AFF:FE79:3F10, Interface ID 3 Area 0.0.0.0, Process ID 1, Instance ID 0, Router ID 192.168.255.11 Network Type BROADCAST, Cost: 12 SHA-1 authentication SPI 2311, secure socket UP (errors: 0) Transmit Delay is 1 sec, State BDR, Priority 1 Designated Router (ID) 192.168.255.15, local address FE80::225:45FF:FE60:17C1 Backup Designated router (ID) 192.168.255.11, local address FE80::21E:7AFF:FE79:3F10 Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:02 Graceful restart helper support enabled Index 1/1/1, flood queue length 0 Next 0x0(0)/0x0(0)/0x0(0) Last flood scan length is 0, maximum is 8 Last flood scan time is 0 msec, maximum is 4 msec Neighbor Count is 2, Adjacent neighbor count is 2 Adjacent with neighbor 192.168.255.14 Adjacent with neighbor 192.168.255.15 (Designated Router) Suppress hello for 0 neighbor(s) R1# R1# R1#show ipv6 ospf neighbor Neighbor ID Pri State Dead Time Interface ID Interface 192.168.255.14 1 FULL/DROTHER 00:00:38 4 FastEthernet0/0 192.168.255.15 1 FULL/DR 00:00:38 4 FastEthernet0/0 R1# R1# R1#show ipv6 ospf neighbor detail Neighbor 192.168.255.14 In the area 0.0.0.0 via interface FastEthernet0/0 Neighbor: interface-id 4, link-local address FE80::215:62FF:FE6A:FEF1 Neighbor priority is 1, State is FULL, 6 state changes DR is 192.168.255.15 BDR is 192.168.255.11 Options is 0x000013 in Hello (V6-Bit, E-Bit, R-bit) Options is 0x000013 in DBD (V6-Bit, E-Bit, R-bit) Dead timer due in 00:00:35 Neighbor is up for 4d23h Index 2/2/2, retransmission queue length 0, number of retransmission 0 First 0x0(0)/0x0(0)/0x0(0) Next 0x0(0)/0x0(0)/0x0(0) Last retransmission scan length is 0, maximum is 0 Last retransmission scan time is 0 msec, maximum is 0 msec Neighbor 192.168.255.15 In the area 0.0.0.0 via interface FastEthernet0/0 Neighbor: interface-id 4, link-local address FE80::225:45FF:FE60:17C1 Neighbor priority is 1, State is FULL, 6 state changes DR is 192.168.255.15 BDR is 192.168.255.11 Options is 0x000013 in Hello (V6-Bit, E-Bit, R-bit) Options is 0x000013 in DBD (V6-Bit, E-Bit, R-bit) Dead timer due in 00:00:36 Neighbor is up for 5d03h Index 1/1/1, retransmission queue length 0, number of retransmission 0 First 0x0(0)/0x0(0)/0x0(0) Next 0x0(0)/0x0(0)/0x0(0) Last retransmission scan length is 0, maximum is 0 Last retransmission scan time is 0 msec, maximum is 0 msec R1# R1# R1#show ipv6 ospf database OSPFv3 Router with ID (192.168.255.11) (Process ID 1) Router Link States (Area 0.0.0.0) ADV Router Age Seq# Fragment ID Link count Bits 192.168.255.11 13 0x8000028F 0 1 E 192.168.255.14 1864 0x8000028F 0 1 E 192.168.255.15 54 0x8000028D 0 1 E Net Link States (Area 0.0.0.0) ADV Router Age Seq# Link ID Rtr count 192.168.255.15 1561 0x8000028D 4 3 Link (Type-8) Link States (Area 0.0.0.0) ADV Router Age Seq# Link ID Interface 192.168.255.11 1010 0x80000287 5 Se0/0/0 192.168.255.11 13 0x80000288 3 Fa0/0 192.168.255.14 1864 0x80000288 4 Fa0/0 192.168.255.15 54 0x80000287 4 Fa0/0 Intra Area Prefix Link States (Area 0.0.0.0) ADV Router Age Seq# Link ID Ref-lstype Ref-LSID 192.168.255.11 13 0x8000028A 0 0x2001 0 192.168.255.14 487 0x8000028C 0 0x2001 0 192.168.255.15 54 0x8000028E 0 0x2001 0 192.168.255.15 54 0x8000028A 4096 0x2002 4 Type-5 AS External Link States ADV Router Age Seq# Prefix 192.168.255.11 1010 0x8000028C 2003:DE:2016:127::/64 192.168.255.11 13 0x800000DE 2003:DE:2016:124::/64 192.168.255.11 1010 0x800000D6 2003:DE:2016:128::/63 192.168.255.11 1010 0x800000D2 2003:DE:2016:1FF::12/127 192.168.255.14 1864 0x80000287 ::/0 192.168.255.15 54 0x80000287 ::/0 R1# R1# R1#show ipv6 ospf summary-prefix OSPFv3 Process 1, Summary-prefix 2003:DE:2016:1FF::12/127 Metric 20, Type 2, Tag 0 R1# R1# R1#show ipv6 route IPv6 Routing Table - default - 16 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea, IS - ISIS summary D - EIGRP, EX - EIGRP external, NM - NEMO, ND - Neighbor Discovery l - LISP O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2 OE2 ::/0 [110/1], tag 1 via FE80::225:45FF:FE60:17C1, FastEthernet0/0 via FE80::215:62FF:FE6A:FEF1, FastEthernet0/0 O 2003:DE:2016:120::/64 [110/13] via FE80::225:45FF:FE60:17C1, FastEthernet0/0 via FE80::215:62FF:FE6A:FEF1, FastEthernet0/0 C 2003:DE:2016:121::/64 [0/0] via FastEthernet0/0, directly connected L 2003:DE:2016:121::42/128 [0/0] via FastEthernet0/0, receive C 2003:DE:2016:122::/127 [0/0] via Serial0/0/0, directly connected L 2003:DE:2016:122::/128 [0/0] via Serial0/0/0, receive D 2003:DE:2016:124::/64 [90/837120] via FE80::21A:6CFF:FEA1:2B98, Serial0/0/0 D 2003:DE:2016:127::/64 [90/834560] via FE80::21A:6CFF:FEA1:2B98, Serial0/0/0 D 2003:DE:2016:128::/63 [90/837120] via FE80::21A:6CFF:FEA1:2B98, Serial0/0/0 LC 2003:DE:2016:1FF::11/128 [0/0] via Loopback0, receive O 2003:DE:2016:1FF::12/127 [110/0] via Null0, directly connected D 2003:DE:2016:1FF::12/128 [90/960000] via FE80::21A:6CFF:FEA1:2B98, Serial0/0/0 D 2003:DE:2016:1FF::13/128 [90/962560] via FE80::21A:6CFF:FEA1:2B98, Serial0/0/0 O 2003:DE:2016:1FF::14/128 [110/12] via FE80::215:62FF:FE6A:FEF1, FastEthernet0/0 O 2003:DE:2016:1FF::15/128 [110/12] via FE80::225:45FF:FE60:17C1, FastEthernet0/0 L FF00::/8 [0/0] via Null0, receive R1# R1# R1#show crypto ipsec sa interface: FastEthernet0/0 Crypto map tag: (none), local addr FE80::21E:7AFF:FE79:3F10 IPsecv6 policy name: OSPFv3-1-2311 IPsecv6-created ACL name: FastEthernet0/0-ipsecv6-ACL protected vrf: (none) local ident (addr/mask/prot/port): (FE80::/10/89/0) remote ident (addr/mask/prot/port): (::/0/89/0) current_peer :: port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 137365, #pkts encrypt: 137365, #pkts digest: 137365 #pkts decaps: 274643, #pkts decrypt: 274643, #pkts verify: 274643 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: FE80::21E:7AFF:FE79:3F10, remote crypto endpt.: :: path mtu 1500, ipv6 mtu 1500, ipv6 mtu idb FastEthernet0/0 current outbound spi: 0x907(2311) PFS (Y/N): N, DH group: none inbound esp sas: inbound ah sas: spi: 0x907(2311) transform: ah-sha-hmac , in use settings ={Transport, } conn id: 2003, flow_id: NETGX:3, sibling_flags 80000001, crypto map: (none) no sa timing replay detection support: N Status: ACTIVE inbound pcp sas: outbound esp sas: outbound ah sas: spi: 0x907(2311) transform: ah-sha-hmac , in use settings ={Transport, } conn id: 2004, flow_id: NETGX:4, sibling_flags 80000001, crypto map: (none) no sa timing replay detection support: N Status: ACTIVE outbound pcp sas: R1# R1# R1#show crypto ipsec policy Crypto IPsec client security policy data Policy name: OSPFv3-1-2311 Policy refcount: 1 Inbound AH SPI: 2311 (0x907) Outbound AH SPI: 2311 (0x907) Inbound AH Key: 3A5F619563BD309F88420946337291284EB74F52 Outbound AH Key: 3A5F619563BD309F88420946337291284EB74F52 Transform set: ah-sha-hmac R1# R1# R1#show ipv6 access-list FastEthernet0/0-ipsecv6-ACL IPv6 access list FastEthernet0/0-ipsecv6-ACL permit 89 FE80::/10 any (274640 matches) sequence 1 R1# |
Featured image “saentis_2017-09-21_32” by Jérôme is licensed under CC BY-NC-SA 2.0.



Great article, thanx Johannes!
When I’m configuring an IPv6 routing interface, I like to statically configure the Link-Local (LL) Interface ID (IID) portion to match the same as I have for the IID portion of a GUA (and/or ULA).
For example, on your R4 loopback interface add ‘ipv6 address fe80::14 link-local’. For R4 g0/0 add ‘ipv6 address fe80::24 link-local’. Now the interfaces v6 IID’s are the same per interface, a little easier to remember.
Where this really provides even more value, the configuration is now portable. The normal default for most L3 switches and routers (that I have worked with) is for the IID to be auto-generated by the OS using the M-EUI-64 format, and if you configure static routes using the neighbor’s LL as required, if a physical neighbor gets replaced, the MAC address of interfaces changes and so does the M-EUI-64 generated address, which therefore means a static route definition is no longer going to work. With the static LL definition, the device configuration file is totally portable – from an IPv6 thinking view at least.
Most L3 switch and router OS’s do support static LL config. What I have found is some firewall OS’s that support v6 routing don’t support static LL config, nor do most client OS’s and some server OS’s.
I’ll say that while doing this is not “required” I consider it an IPv6 “best practice”.
Thanx again…Jeff