This is a small tutorial for configuring a site-to-site IPsec VPN between a Palo Alto and a FortiGate firewall. I am publishing step-by-step screenshots for both firewalls as well as a few troubleshooting CLI commands.
Lab
This is my basic laboratory for this VPN connection. I am using a Palo Alto PA-200 with PAN-OS 6.1.1 while the FortiWiFi 90D has v5.2.2 installed.
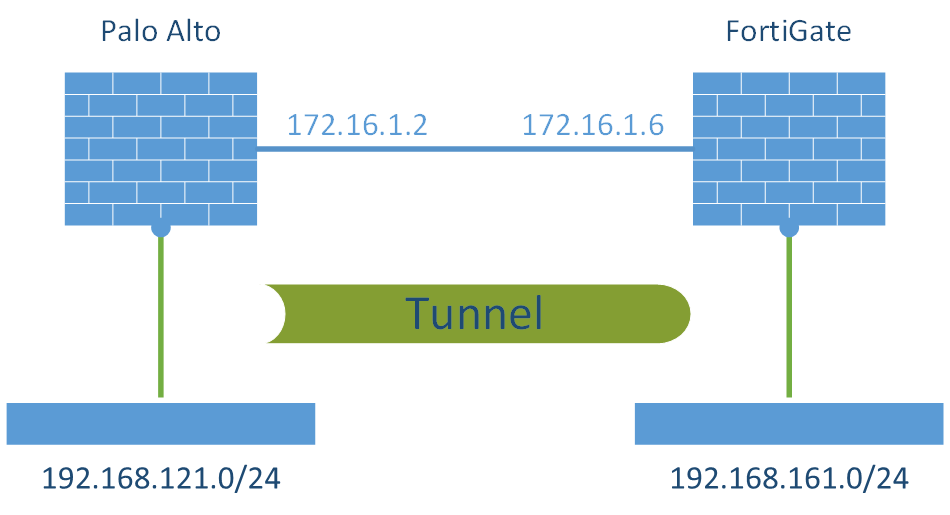
Please note that I am only showing the steps to configure the VPN (phase 1 + phase 2, i.e., IKE and IPsec/ESP), while I am NOT showing the mandatory security policies to actually allow traffic passing the firewalls. You must add appropriate security policies from the VPN zones to the internal zones (and vice versa) by yourself.
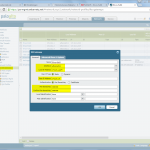
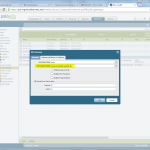
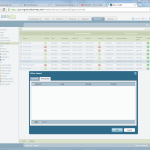
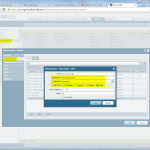
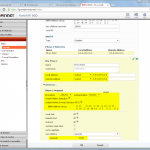
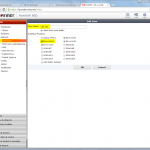
Palo Alto
The Palo Alto is configured in the following way. Please refer to the descriptions under the images for detailed information.
(And do not forget the “untrust-untrust” policy that allows ipsec!)
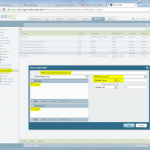
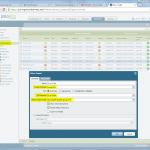
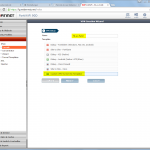
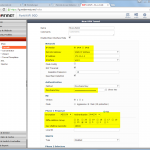
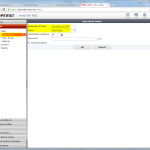
FortiGate
And this is the way for the FortiGate firewall:
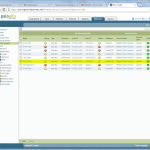
Monitoring
Following are a few screenshots and listings from both firewalls concerning the VPN:
Palo Alto CLI:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
weberjoh@fd-wv-fw02> show vpn ike-sa gateway fd-wv-fw04 phase-1 SAs GwID/client IP Peer-Address Gateway Name Role Mode Algorithm Established Expiration V ST Xt Phase2 --------------- ------------ ------------ ---- ---- --------- ----------- ---------- - -- -- ------ 10 172.16.1.6 fd-wv-fw04 Resp Main PSK/DH14/A256/SHA256 Jan.20 11:12:57 Jan.20 19:12:57 v1 12 2 1 Show IKEv1 IKE SA: Total 1 gateways found. 1 ike sa found. phase-2 SAs GwID/client IP Peer-Address Gateway Name Role Algorithm SPI(in) SPI(out) MsgID ST Xt --------------- ------------ ------------ ---- --------- ------- -------- ----- -- -- 10 172.16.1.6 fd-wv-fw04 Resp DH14/tunl/ESP/A256/SHA256 A3D05151 C97B0AB3 C5572823 9 1 Show IKEv1 phase2 SA: Total 1 gateways found. 1 ike sa found. |
FortiGate CLI:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 |
fd-wv-fw04 # get vpn ike gateway fd-wv-fw02 vd: root/0 name: fd-wv-fw02 version: 1 interface: wan1 6 addr: 172.16.1.6:500 -> 172.16.1.2:500 created: 572s ago IKE SA created: 1/1 established: 1/1 time: 70/70/70 ms IPsec SA created: 1/1 established: 1/1 time: 90/90/90 ms id/spi: 20057 2b5ce64a51119571/defa8a4a3a5f0573 direction: initiator status: established 572-572s ago = 70ms proposal: aes-256-sha256 key: ed29b2dc34c59b46-c587e9daee5d91fb-d83448f2f91bcbae-60505b8efc09fb72 lifetime/rekey: 28800/27927 DPD sent/recv: 0000006e/00000000 fd-wv-fw04 # fd-wv-fw04 # fd-wv-fw04 # get vpn ipsec tunnel name fd-wv-fw02 gateway name: 'fd-wv-fw02' type: route-based local-gateway: 172.16.1.6:0 (static) remote-gateway: 172.16.1.2:0 (static) mode: ike-v1 interface: 'wan1' (6) rx packets: 641 bytes: 65776 errors: 0 tx packets: 642 bytes: 168 errors: 1 dpd: enabled/negotiated idle: 5000ms retry: 3 count: 0 selectors name: 'fd-wv-fw02' auto-negotiate: disable mode: tunnel src: 0:0.0.0.0/0.0.0.0:0 dst: 0:0.0.0.0/0.0.0.0:0 SA lifetime/rekey: 3600/2907 mtu: 1438 tx-esp-seq: 280 replay: enabled inbound spi: c97b0ab3 enc: aes 51128eb018d1ba7bc1e701f2c98689895df63dd1ca0c0252a07b178c5b867652 auth: sha256 66b3dee1523d2aefd008e3d350a140133b76ebcb768974d6142c4d2f118c0862 outbound spi: a3d05151 enc: aes f168c4dc08b795dc978a4def5979acdc4aa7fbf0bedc1a1c4271bd2cbfe76f40 auth: sha256 353c678f8ff1e782b3c59eed1628e80a574f2162f4ac5d38cbffe58e538dd064 NPU acceleration: encryption(outbound) decryption(inbound) |

We followed step by step for this lab set up and the tunnel isn’t even coming up. Do you have any suggestions that might be the reason for this?
;) You should at least tell me a bit more about your error logs, etc. Simply saying “it is not working – can you tell me the issue” is like “let me look into my crystal ball”…
Please have a look at the log entries on both firewalls and try to find the issue then.
The above steps are incomplete as you need to define the proxy ID’s, the peer and local id’s on the ike gateway and double check your IKE gateway on both sides, Fortigate does not like to negotiate child SA’s cleanly.
Takes a while for the Fortigate to play nicely.
Other than that, the article is a great step-by-step guide
please could you explain more detail. i’m using fortigate. and other site is using paloalto. how can i define the proxy id, peer, local id
??? What do you mean with more detail? Absolutely everything is explained in the screenshots above. ;)
You need NOT define any proxy IDs. Everything is done with the routing!
You also need NOT define the local id, if the VPN is between static IP addresses.
Hi Johannes,
were there any IPv4 policies created for the Fortigate firewall in your Site-to-Site setup?
I’m also having an issue.
have setup a VPN from my PA to a Fortigate FW in main mode. no proxy IDs, or local/remote IDs are used.
here is the error:
IKE phase-2 negotiation failed when processing proxy ID. cannot find matching phase-2 tunnel for received proxy ID. received local id: x.x.x.x/32 type IPv4_address protocol 0 port 0, received remote id: x.x.x.x/32 type IPv4_address protocol 0 port 0.
it feels like I’m hitting a policy-based VPN setup, but I’m assured it is a route-based setup. I’m not sure why it is complaining about the Proxy ID?
any suggestions?
Hey Justin,
even if you’re using a “route-based” VPN, proxy IDs of type 0.0.0.0/0 (or ::/0 for IPv6) are announced. That is: Both firewalls implicitly list this 0.0.0.0/0 entry when you’re not configuring anything else.
Note that your error message looks like you have configured a proxy ID with 0.0.0.0/32. It must be 0.0.0.0/0 to have “any”. If you are not sure, configure a 0.0.0.0/0 on BOTH firewalls.
And keep on looking at the error logs on both firewalls as well. The better logs are generated at the receiving side, not at the initiating side.
Hey there,
Nice blog, but this tutorial is thoroughly incomplete. And people are trying to tell you that, yet you seem to be oblivious to it.
Both the peers need security policies to pass the actual traffic.
On the fortigate side we need:
FortiGate-VM64 # show firewall policy
config firewall policy
edit 1
set name “vpn_fgt-pan-test_local”
set uuid 8458dc14-a089-51e8-514e-a99143ce576e
set srcintf “port3”
set dstintf “fgt-pan-test”
set srcaddr “fgt-pan-test_local”
set dstaddr “fgt-pan-test_remote”
set action accept
set schedule “always”
set service “ALL”
set comments “VPN: fgt-pan-test (Created by VPN wizard)”
next
edit 2
set name “vpn_fgt-pan-test_remote”
set uuid 845b9d1e-a089-51e8-563b-2bdbbf9f2382
set srcintf “fgt-pan-test”
set dstintf “port3”
set srcaddr “fgt-pan-test_remote”
set dstaddr “fgt-pan-test_local”
set action accept
set schedule “always”
set service “ALL”
set comments “VPN: fgt-pan-test (Created by VPN wizard)”
next
end
And the palo alto side, we need vpn zone to inside/dmz policies with apps you need.
admin@PA-FW1# show rulebase security rules vpn-inside
vpn-inside {
to inside;
from ipsec-vpn;
source any;
destination any;
source-user any;
category any;
application any;
service application-default;
hip-profiles any;
action allow;
disabled yes;
}
Also you can add selectors to both fortigate and palo alto, on PA they are called proxy id (very stupid name).
On fortigate they are called phase 2 selectors in phase 2 part of the config.
If only the peer has selectors and proxy ids are not configured on the PA then you will see
2018-08-16 13:27:02 [INTERNAL_ERR]: isakmp_quick.c:1994:get_sainfo_r(): can’t find matching selector
2018-08-16 13:27:02 [PROTO_ERR]: isakmp_quick.c:1209:quick_r1recv(): failed to get sainfo.
2018-08-16 13:27:02 [INTERNAL_ERR]: ikev1.c:1631:isakmp_ph2begin_r(): failed to pre-process packet.
Hi allwyn,
thanks for the hint. I have added a sentence to the post that I’m not showing the security policies here.
Cheers,
Johannes
It would be actually nice to assign/use /30 subnet for Tunnel interfaces ,so that you can enable IPSEC tunnel monitoring . Plus , the static routes would look nicer and cleaner .
BTW , Palo Alto doesn’t trully support proxy based VPN , it’s a proxy based VPN termination with matching Proxy IDs to match for example Cisco encryption domains .
For the Fortinet side of things …… People leave quick selectors alone … just 0.0.0.0/0.0.0.0 .. it means I’m encrypting whatever but the source and dest traffic is being controlled by 1. Static routes via Tunnel interface 2. Bidirectional security policies .
I have a PA200 that I am trying to connect to a PFSense router using ipsec VPN. Both are on two different internet connections. PFsense connects fine I can see the IKE connection and it shows on the Palo as connected but the tunnel is red. Can’t see either sides networks. I have a static route to the pfsense side as 192.168.2.x/24 and on the palo side I have the zones setup with the zones and tunnel interface but no traffic flows.
Hello. I have created two VPN tunnels between the two firewalls all is well. but when I want to apply the BFD on the palo alto tunnel it tells me that the tunnel needs a ip adresse. do have any idea aboute This issue. Thanks
Well, for BFD to work you have to use IP addresses on the tunnel interfaces. ;) Fortunately, you can use IP addresses on the tunnel interfaces on both sides, Palo and Forti. However, I don’t know whether or not you can use BFD on the Forti. (Currently, I can’t even use it on the Palo since my PA-220 does not implement it.)
There’s nothing incomplete about this article. It’s a goddamn firewall, of course you need to allow ike and ipsec traffic biderectionally before anything works.
Thanks for this article. Had to deal with a customer using a Fortigate and the screenshots helped me point them in the right direction.