Similar to all my other site-to-site VPN articles, here are the configurations for a VPN tunnel between a Juniper ScreenOS SSG firewall and a Cisco IOS router. Due to the VPN Monitor of the SSG firewall, the tunnel is established directly after the configuration and stays active all the time without the need of “real” traffic.
I am using the policy-based VPN solution on the Cisco router and not the virtual tunnel interface (VTI) approach. That is: No route is needed on the router while the Proxy IDs must be set on the Juniper firewall. (However, I also documented the route-based VPN solution between a ScreenOS firewall and a Cisco router here.)
Laboratory
This figure shows my lab:
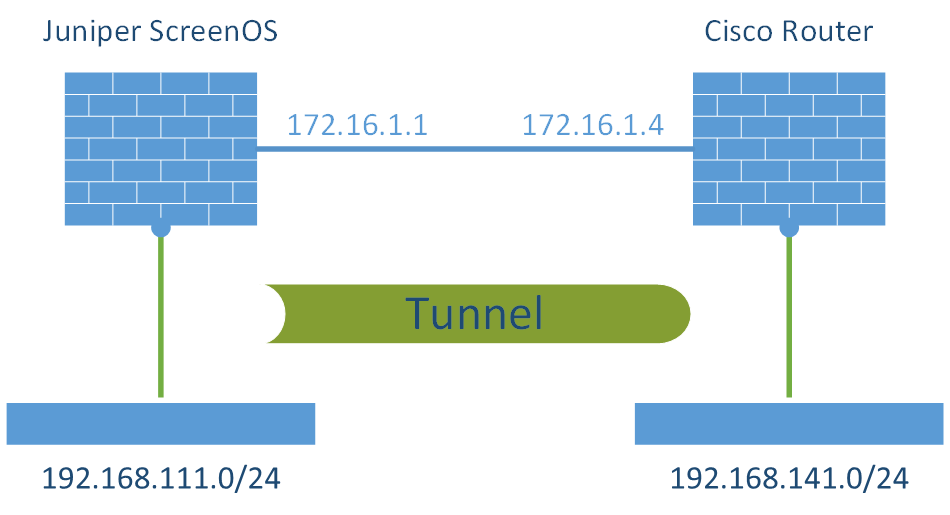
My Juniper SSG 5 firewall ran at version 6.3.0r17.0. The (old) Cisco router 2621 had IOS 12.3(26) installed (c2600-ik9o3s3-mz.123-26.bin).
Juniper ScreenOS SSG
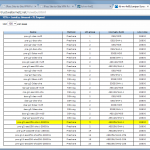
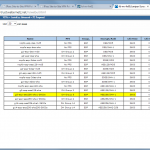
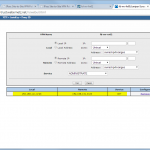
The configuration steps on the SSG are the following:
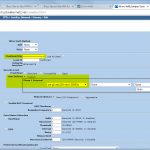
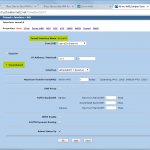
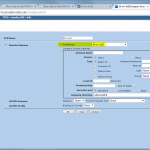
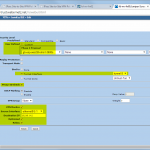
- P1 and P2 Proposals, e.g., PFS group 5, AES256, SHA1, 28800/3600 sec.
- Gateway with Preshared Key and P1 Proposal.
- Unnumbered Tunnel Interface.
- AutoKey IKE profile which points to the just created gateway, P2 proposal and tunnel interface. The checkmark “Proxy-ID Check” is mandatory here. Furthermore, the VPN Monitor can be set to automatically build the tunnel.
- Proxy ID(s) corresponding to the tunneled networks.
- Specific route through the tunnel interface.
Here are my configuration screenshots:
Cisco Router
The listing below shows all relevant commands for the VPN tunnel. Of course, the isakmp policy and the ipsec transform-set is identical to the ones I configured on the Juniper firewall. Note that I also configured the “hash sha” command inside the “crypto isakmp policy 10” submenu. However, this is not shown since it seems to be the default value. Same on the “set security-association lifetime seconds 3600” command inside the “crypto map map01 2 ipsec-isakmp” submenu.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
! crypto isakmp policy 10 encr aes 256 authentication pre-share group 5 lifetime 28800 ! crypto isakmp key 5aSZlgNGDwHfhcYmnTWxmLM53YXjE6 address 172.16.1.1 ! crypto ipsec transform-set aes256-sha esp-aes 256 esp-sha-hmac ! crypto map map01 2 ipsec-isakmp set peer 172.16.1.1 set transform-set aes256-sha set pfs group5 match address acl-vpn-SSG ! interface FastEthernet0/0 crypto map map01 ! ip access-list extended acl-vpn-SSG permit ip 192.168.141.0 0.0.0.255 192.168.111.0 0.0.0.255 ! |
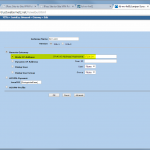
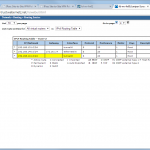
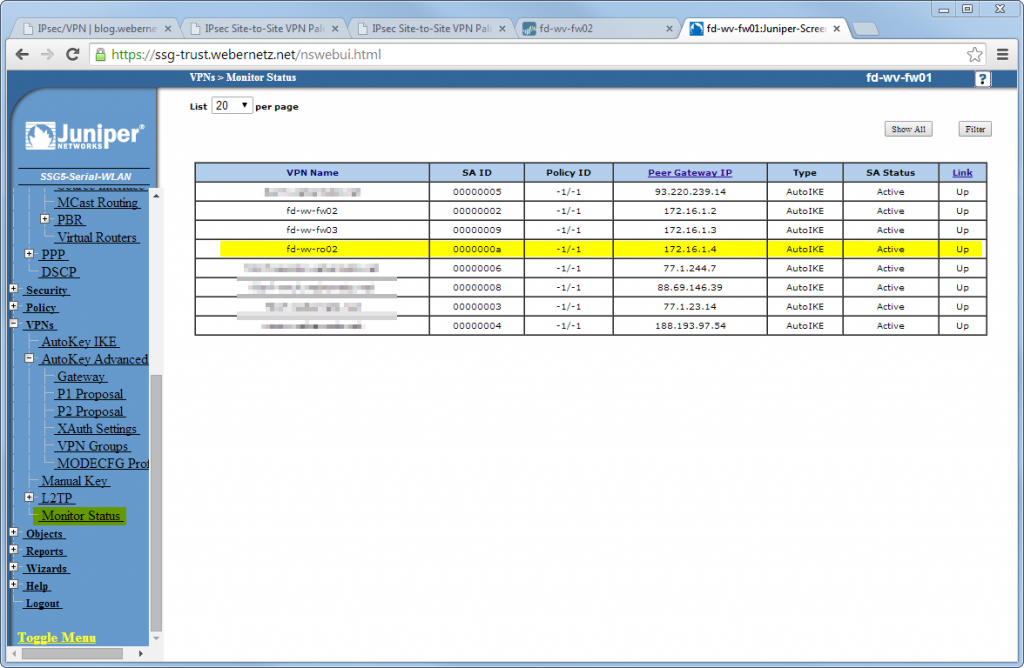
It’s running :)
As the Monitor Status of the Juniper reveals:
The Cisco router can be queried with the following commands:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 |
fd-wv-ro02#show crypto isakmp sa detail Codes: C - IKE configuration mode, D - Dead Peer Detection K - Keepalives, N - NAT-traversal X - IKE Extended Authentication psk - Preshared key, rsig - RSA signature renc - RSA encryption C-id Local Remote I-VRF Encr Hash Auth DH Lifetime Cap. 512 172.16.1.4 172.16.1.1 aes sha psk 5 03:05:51 ------------------------------------------------------------------------------- fd-wv-ro02#show crypto ipsec sa interface: FastEthernet0/0 Crypto map tag: map01, local addr. 172.16.1.4 protected vrf: local ident (addr/mask/prot/port): (192.168.141.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (192.168.111.0/255.255.255.0/0/0) current_peer: 172.16.1.1:500 PERMIT, flags={origin_is_acl,} #pkts encaps: 4937, #pkts encrypt: 4937, #pkts digest 4937 #pkts decaps: 4937, #pkts decrypt: 4937, #pkts verify 4937 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 172.16.1.4, remote crypto endpt.: 172.16.1.1 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0 current outbound spi: 38F5083A inbound esp sas: spi: 0xA0608BB1(2690681777) transform: esp-256-aes esp-sha-hmac , in use settings ={Tunnel, } slot: 0, conn id: 2088, flow_id: 89, crypto map: map01 sa timing: remaining key lifetime (k/sec): (4418894/3383) IV size: 16 bytes replay detection support: Y inbound ah sas: inbound pcp sas: outbound esp sas: spi: 0x38F5083A(955582522) transform: esp-256-aes esp-sha-hmac , in use settings ={Tunnel, } slot: 0, conn id: 2089, flow_id: 90, crypto map: map01 sa timing: remaining key lifetime (k/sec): (4418894/3383) IV size: 16 bytes replay detection support: Y outbound ah sas: outbound pcp sas: ------------------------------------------------------------------------------- fd-wv-ro02#show crypto map Crypto Map "map01" 2 ipsec-isakmp Peer = 172.16.1.1 Extended IP access list acl-vpn-SSG access-list acl-vpn-SSG permit ip 192.168.141.0 0.0.0.255 192.168.111.0 0.0.0.255 Current peer: 172.16.1.1 Security association lifetime: 4608000 kilobytes/3600 seconds PFS (Y/N): Y DH group: group5 Transform sets={ aes256-sha, } Interfaces using crypto map map01: FastEthernet0/0 |