This is a guest blogpost by Erik Hjelmvik, an expert in network forensics and network security monitoring at NETRESEC.
Wireshark is the default goto tool for analyzing captured network traffic for most network engineers. But there are a few other free and open source alternatives that are sometimes overlooked, one of which is NetworkMiner (disclaimer: I’m the creator of NetworkMiner).
Extracting Files from PCAP Files
Many users turn to NetworkMiner when it comes to extracting artifacts, such as files or credentials from pcap files. You can solve such tasks with Wireshark too, but NetworkMiner will save you time and spare you some tedious manual work. In fact, NetworkMiner automatically extracts files from protocols like FTP, TFTP, HTTP, HTTP/2, SMB, SMB2, SMTP, POP3, and IMAP as soon as a pcap file is opened.
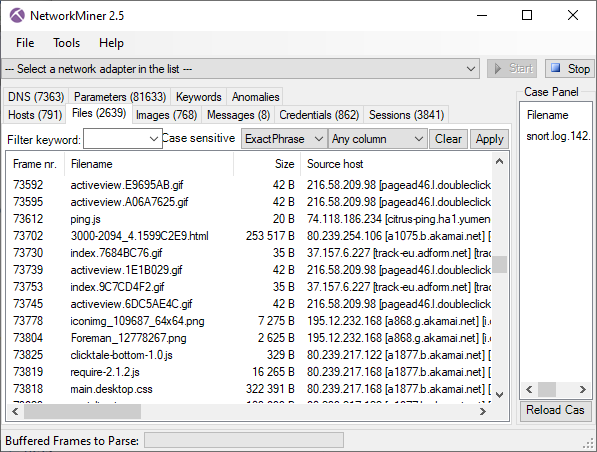
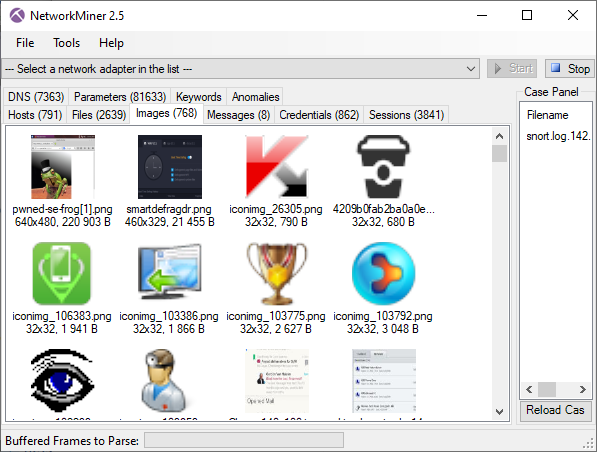
Extracted files that are recognized as images are also shown as thumbnails on the images tab. This image list can give a quick overview of what is going on in the capture file.
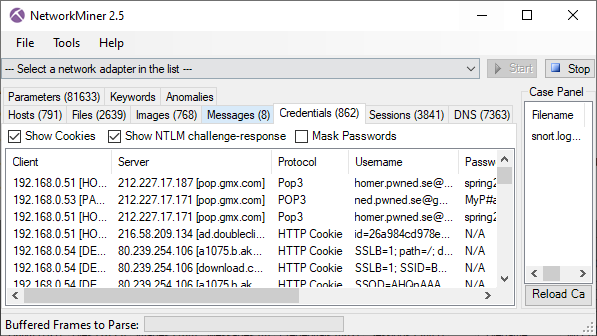
Usernames and Passwords
User credentials, such as usernames, passwords and hashes that NetworkMiner detects are all placed under the “Credentials” tab. The protocols and data structures from which NetworkMiner can extract credentials include FTP, HTTP cookies, HTTP POST requests, IMAP, Kerberos hashes, MS SQL, NTLM hashes, POP3, RDP cookies, SMTP, SOCKS and a few more.
Passive Host Inventory
Another popular feature in NetworkMiner is the “Hosts” tab, which provides an overview of which devices have been observed in the loaded capture files. NetworkMiner aggregates data based on IP address in the Hosts tab, which is useful if you want to create a host inventory list without actively scanning a network or if you want to learn more about a particular IP address.
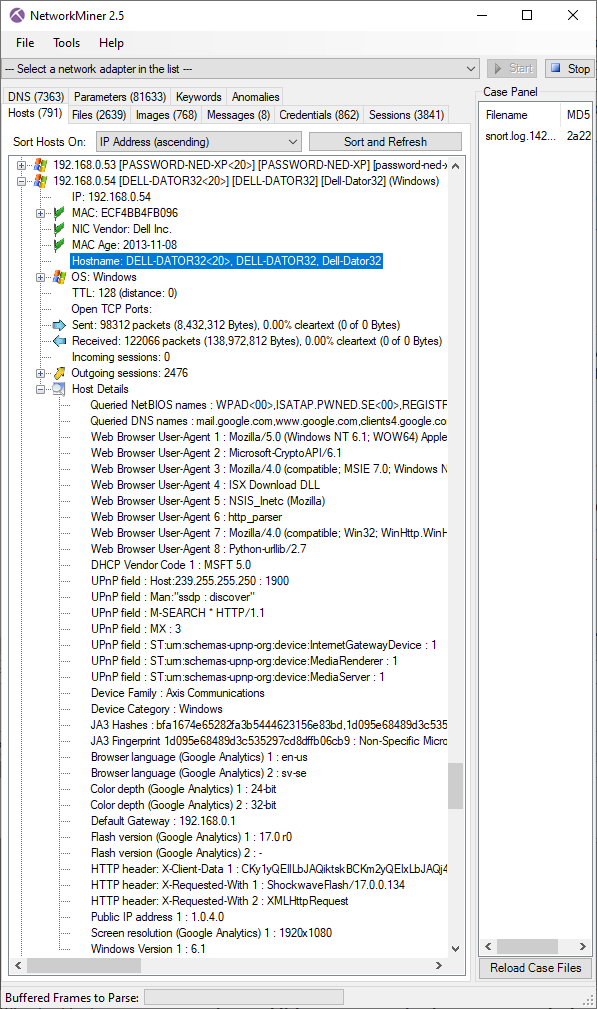
The Hosts tab is great if you want to find out what hostname(s) an IP address has since it doesn’t just rely on captured DNS traffic to perform passive hostname resolution. NetworkMiner also extracts and aggregates hostname info from the CIFS Browser Protocol, DHCP, HP Switch Protocol, HTTP/2 authority headers, HTTP host headers, HTTP User-Agent strings, Kerberos, NetBIOS Datagram Service, NetBIOS Name Service, NTLMSSP, TLS SNI, X.509 certificates, and a few additional protocols and data structures.
The Hosts tab is also often used in order to find out which operating system a host is running as well as details like what web browser User-Agents or open SMB file shares it has.
Windows Only?
NetworkMiner is primarily a Windows tool, but it can also be run in Linux if you install Mono. You can even run NetworkMiner on macOS with help of Mono, but the Mono support on macOS is unfortunately not as good as in Linux.
So why not give NetworkMiner a try next time you want to extract a few files from a capture file or get an overview of what’s going on in a capture? It’s a free tool that doesn’t even require an installation, you just extract the zip file and run it!
The capture file loaded into NetworkMiner in the screenshots above is “snort.log.1426204807” from the FIRST 2015 “Hands-on Network Forensics” training PCAP dataset. You can download this capture file, and many more, from Netresec’s Publicly available PCAP files.



I’ve worked with Network Miner in many cases. I think it is a valuable addition to Wireshark, it saves a lot of time when working with files and host discovery.