DNS-based Authentication of Named Entities (DANE) is a great feature that uses the advantages of a DNSSEC signed zone in order to tell the client which TLS certificate he has to expect when connecting to a secure destination over HTTPS or SMTPS. Via a secure channel (DNSSEC) the client can request the public key of the server. This means, that a Man-in-the-Middle attack (MITM) with a spoofed certificate would be exposed directly, i.e., is not possible anymore. Furthermore, the trust to certificate authorities (CAs) is not needed anymore.
In this blog post, I will show how to use DANE and its DNS records within an authoritative DNS server to provide enhanced security features for the public.
In my last posts, I covered a secure installation of BIND as an authoritative DNS server, as well as the implementation of DNSSEC. This is really mandatory because without a signed DNS zone DANE would be useless. Though I am using BIND for the examples below, DANE can be used with any other DNS server, too.
What’s DANE?
The abstract of RFC 6698 “The DNS-Based Authentication of Named Entities (DANE) Transport Layer Security (TLS) Protocol: TLSA”, in which DANE is proposed, describes pretty well what DANE is: “Encrypted communication on the Internet often uses Transport Layer Security (TLS), which depends on third parties to certify the keys used. This document improves on that situation by enabling the administrators of domain names to specify the keys used in that domain’s TLS servers. This requires matching improvements in TLS client software, but no change in TLS server software.”
Today, a browser establishes a secure TLS connection to a known server (DNS name) with an “unknown” certificate (not proved by the end-user). We are relying on certificate authorities (CAs), which once verified the certificate to be owned by the server operator. Unluckily, any (!) CA is able to sign every (!) certificate in the world, even if a certificate is NOT owned by the server itself, but by a malicious third party that wants to intercept the secure communication via a man-in-the-middle (MITM) attack.
With the new DNS resource record “TLSA”, the hashed public key is publicized within the DNS server of the same authority/entity that owns the TLS server, e.g., an HTTPS server or an SMTPS mail gateway. Now, an end-user client can really validate that the server TLS certificate is owned by the same organization which owns the DNSSEC server. Hence, MITM attacks with spoofed certificates are not possible anymore.
For more information about DANE, refer to the RFCs: 6698, 7218, 7671, and 7672.
Generate TLSA Records
No changes must be made by the TLS servers. The only thing to do is to place the hashed public key into the DNS zone. For the most common scenarios, the fields within the TLSA record are the following (refer to RFC 7671, section 5.1):
- Usage: 3 – DANE-EE: Domain Issued Certificate
- Selector: 1 – SPKI: Use subject public key
- Matching-Type: 1 – SHA-256
For an on-site generation of TLSA records the tool “tlsa” out of the “hash-slinger” toolkit can be used. On a Ubuntu server, this works as follows:
|
1 2 3 |
weberjoh@jw-nb12-lx:~$ sudo apt-get install hash-slinger weberjoh@jw-nb12-lx:~$ tlsa --create --selector 1 --certificate host-dane.weberdns.de.crt host-dane.weberdns.de _443._tcp.host-dane.weberdns.de. IN TLSA 3 1 1 0d6fce3320315023ff499a3f3de1c362c88f8380311ac8c036890dab13243aa7 |
An easy-to-use online tool by Shumon Huque is here: Generate TLSA Record. Copy and paste your certificate, etc., and choose the selector field of “0 – Cert”:
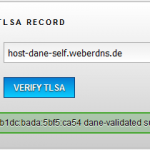
In any way, the TLSA resource record for my test domain “host-dane.weberdns.de” is this:
|
1 |
_443._tcp.host-dane.weberdns.de. IN TLSA 3 1 1 0d6fce3320315023ff499a3f3de1c362c88f8380311ac8c036890dab13243aa7 |
This string must be placed into the appropriate zone file on the DNSSEC signing server, in my case “weberdns.de”. After that, I can manually test/request the TLSA record _443._tcp. ... via DNS and can see that it is authentic (AD flag):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
weberjoh@jw-nb12-lx:~$ dig _443._tcp.host-dane.weberdns.de tlsa +dnssec +multi ; <<>> DiG 9.10.3-P4-Ubuntu <<>> _443._tcp.host-dane.weberdns.de tlsa +dnssec +multi ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 59953 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;_443._tcp.host-dane.weberdns.de. IN TLSA ;; ANSWER SECTION: _443._tcp.host-dane.weberdns.de. 3066 IN TLSA 3 1 1 ( 0D6FCE3320315023FF499A3F3DE1C362C88F8380311A C8C036890DAB13243AA7 ) _443._tcp.host-dane.weberdns.de. 3066 IN RRSIG TLSA 8 5 3600 ( 20160929094014 20160830084014 57909 weberdns.de. aZgVX1C6uxACoNnPo4m36CRzMjfe2Gk7pciV2knGrb5P Hbq1UV/u2EdFJD6v5Dhd4JAquuM7OW9CQVfE1f0g380/ HsUMzg6eZeOr3sMR2ERZXv4hut4sikdtjGhVmA6jSbfg EQFM0BELYz/+Xzh9uJYoqzkbJ54uKCpapaWgELs= ) ;; Query time: 1 msec ;; SERVER: 192.168.120.22#53(192.168.120.22) ;; WHEN: Tue Aug 30 11:50:16 CEST 2016 ;; MSG SIZE rcvd: 278 |
Examples
I generated three different TLSA records for my test domains (IPv6-only):
- host-dane.weberdns.de <- with a trusted CA-signed certificate
- host-dane-self.weberdns.de <- with a self-signed (!) certificate
- mail.weberdns.de <- with a CA-signed certificate whose FQDN is NOT mail.weberdns.de
The appropriate TLSA records are the following. Note that I have some different usage and matching type fields, e.g., SHA256 and SHA512:
|
1 2 3 4 |
_443._tcp.host-dane.weberdns.de. IN TLSA 3 1 1 0d6fce3320315023ff499a3f3de1c362c88f8380311ac8c036890dab13243aa7 _443._tcp.host-dane-self.weberdns.de. IN TLSA 3 1 1 97b57e11a9f07976ae0a44b3d68179e61637f3ca43b719a149f8d524c0dc2405 _443._tcp.host-dane-self.weberdns.de. IN TLSA 3 1 2 bab6316ace46fdce7028ea0100c4c0c364dc2f092258f8958b9ab1bde89c73ade3bd37aebf54245268128b039114e760b6a0d79e366c8c0b396884ab4287a05a _25._tcp.mail.weberdns.de. IN TLSA 3 0 1 ae822a14fd5e56c213eeeb5d6755556980caf4c3f2531c1ec8eca3076f9b7e68 |
Note that in all three cases, a TLSA check is valid though only the first TLS certificate is correctly signed by a trusted CA with its correct common name! This is the main advantage of DANE, that self-signed certificates can be used, even with incorrect names, as long as the certificate itself is the correct one published in the DNS.
Online Tools
There are great online tools for checking TLSA records either for HTTPS or for SMTPS:
- Verify a DANE TLSA Record by SIDN Labs <- for HTTPS
- Check a DANE TLS Service by Shumon Huque <- for many protocols, incl. SMTPS w/ STARTTLS
- DANE SMTP Validator by sys4 <- SMTPS
- DANE Validator by DANEtools <- for many protocols but buggy
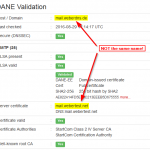
Here are two sample screenshots of the tools for my test domains. The “host-dane-self” domain is valid though self-signed, while the “mail.weberdns.de” is valid, too, though not congruent with the name of the certificate:
A more detailed view is the text output from Shumon’s SMTPS test with STARTTLS. It greatly shows the connection (via IPv4 and IPv6), the common name of the cert, as well as the matching TLSA record:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 |
TLSA records found: 1 TLSA: 3 0 1 ae822a14fd5e56c213eeeb5d6755556980caf4c3f2531c1ec8eca3076f9b7e68 Connecting to IPv6 address: 2003:51:6012:110::15 port 25 recv: 220 mail.webertest.net ESMTP send: EHLO cheetara.huque.com recv: 250-mail.webertest.net recv: 250-8BITMIME recv: 250-SIZE 10485760 recv: 250 STARTTLS send: STARTTLS recv: 220 Go ahead with TLS TLSv1.2 handshake succeeded. Cipher: SSLv3 DHE-RSA-AES256-SHA Peer Certificate chain: 0 Subject CN: mail.webertest.net Issuer CN: StartCom Class 2 IV Server CA 1 Subject CN: StartCom Class 2 IV Server CA Issuer CN: StartCom Certification Authority SAN dNSName: mail.webertest.net DANE TLSA 3 0 1 [ae822a14fd5e...] matched EE certificate at depth 0 Validated Certificate chain: 0 Subject CN: mail.webertest.net Issuer CN: StartCom Class 2 IV Server CA SAN dNSName: mail.webertest.net Connecting to IPv4 address: 80.154.108.237 port 25 recv: 220 mail.webertest.net ESMTP send: EHLO cheetara.huque.com recv: 250-mail.webertest.net recv: 250-8BITMIME recv: 250-SIZE 10485760 recv: 250 STARTTLS send: STARTTLS recv: 220 Go ahead with TLS TLSv1.2 handshake succeeded. Cipher: SSLv3 DHE-RSA-AES256-SHA Peer Certificate chain: 0 Subject CN: mail.webertest.net Issuer CN: StartCom Class 2 IV Server CA 1 Subject CN: StartCom Class 2 IV Server CA Issuer CN: StartCom Certification Authority SAN dNSName: mail.webertest.net DANE TLSA 3 0 1 [ae822a14fd5e...] matched EE certificate at depth 0 Validated Certificate chain: 0 Subject CN: mail.webertest.net Issuer CN: StartCom Class 2 IV Server CA SAN dNSName: mail.webertest.net |
And by the way, for more information about DANE, have a look at the common mistakes help page from “sys4” as well.
Browser Add-On: DNSSEC/TLSA Validator
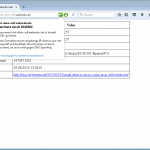
The only good browser plugin for checking DNSSEC and DANE records is the “DNSSEC/TLSA Validator“. Unluckily it has not been updated for almost two years (as of October 2016) and I ran into some Firefox errors while this plugin was enabled.
However, for some tests, it shows the status of the DNS name (first green icon) as well as the DANE/TLSA status (second green icon):
Problem: SSL Interception
One problem will arise if browsers do their own DANE check (which is unluckily not happening today) while organizations are using SSL/TLS interception at their firewalls/proxies. In these cases, the SSL man-in-the-middle “attack” will spoof the certificate to an own created one which is signed by the organizations CA. Though this CA is installed in the browsers, the TLSA check will fail. To my mind, the only way to accomplish this (while not stopping the MITM) is the creation of an “Island of Trust” for DNSSEC with real-time TLSA record spoofing. (Any other ideas?)
Conclusion
That was easy! With only some little DNS resource records, much more security, i.e., authentication, can be achieved. Browsers can access self-signed websites without relying on (malicious) CAs, and MTAs (mail transfer agents) can send mails with the usage of TLS directly to the correct (authentic) destinations.
Today (2016), we are still stuck in the chicken-or-egg problem: Only some sites have DNSSEC signed TLSA records while only some end systems (browsers, MTAs) can validate them. To overcome this problem: Start signing your DNS zones now and insert as many TLSA records as you can. ;)
Featured image “KW5-Nummer-Martin” by Martin Ilich is licensed under CC BY-SA 2.0.





Thanks for this. FYI, beginning with BIND 9.11.0, BIND will return TLSA records (if present) in the additional section when responding to a request for MX or SRV records.
Hii ..According to the example which you explained you have a live domain registered with domain registery. I have a doubt, For example if we are running a completely private domain including root node and Top level domain without registering to the Domain registery , Is it possible to develop DNSSEC Hierarchy by our own and then implement DANE and TLSA over it?. Because normally in live domains according to DNSSEC hierarchy the hashed DS segment of the child node is stored in parent in domain registery.But how to implement for a completely private network?
Hey Henderson,
you are correct that all of my examples are real “live” domains. Just as the Internet works with its single root. ;)
And yes, you can use DNSSEC for private/hidden domains. The DNSSEC validating resolvers simply need your “trust anchors”, which is the KSK, type 257. For example, BIND uses the “bind.keys” file which currently has the two KSKs for the “.” root domain. You can add your “private.domain.tld” KSK there. Or you can completely override the root domain with your own root KSK. But be sure about what you’re doing! When you’re overriding the root KSK you might get other problems when your using DNSSEC with “real” Internet domains.
(And of course you can then use any other DNSSEC related feature such as DANE/TLSA or SSHFP with that.)
Ciao,
Johannes
A crucial part of implementing DANE is planning for key/cert rollover. This means that at least some of the time, a single TLSA record is not enough. At least one of the TLSA records needs to match the “previous” certificate chain, and at least another needs to match the “future” certificate chain.
Introducing a second TLSA record a few DNS TTLs before rollover and then removing the original after can be a complicated process to execute correctly.
Therefore, for the majority of DANE users, I *strongly* recommend that they *always* have at least two TLSA records, only *one* of which changes at the next key/cert replacement.
The two approaches are:
1. 3 1 1 (current) + 3 1 1 (next)
2. 3 1 1 (volatile) + 2 1 1 (stable)
With the first approach the key for the next rotation cycle is generated as soon as the current key is deployed. The TLSA record is then computed, and pre-published in the DNS (along with the 3 1 1 record for the new live key) as soon as the new key goes live. Later, when it is time to generate a new certificate, the pre-generated key is used, and the process repeats.
With the second approach (potentially less secure when using a third-party CA) the stable “2 1 1” key that matches the key of an intermediate issuer CA (or root CA, but then the root CA MUST appear in the server’s full chain file, which users tend to neglect to do) ensures that DANE continues to work even as the server’s key is changed and the “3 1 1” record becomes stale. After the rollover, a new “3 1 1” is generated and published, making both records valid again. When the issuer key is about to change, the server must then make sure to use the same key as before to obtain a new certificate from the same issuer, and in that case replace the “2 1 1” record after the rollover.
Regardless of the approach, MONORING and good scripting of the process (perhaps fully automated) is critical, so that key steps are not forgotten if done by hand.
So my advice is by all means, please, implement DANE… BUT ONLY if you’re prepared to do it properly. Security is not “deploy and forget”, it needs to be monitored and properly planned. DO NOT deploy DANE as a mere fashion statement:
https://dane.sys4.de/common_mistakes#1
https://imrryr.org/~viktor/ICANN61-viktor.pdf
https://imrryr.org/~viktor/icann61-viktor.mp3
This makes it perfectly clear again. That security engineers should get out of their bubble and design mechanisms which are easy to implement. I understand how DANE works but for people who don’t deal with this on a daily base, good luck!
There is no way it will be widely adapted (it’s here since ages now) anytime soon, no wonder why browsers ignore it.
IMHO the risk for availability is higher then the risk for an integrity failure (MITM).
Nevertheless Viktor: excellent read!
Great post,
I wonder about port 25? You put it into the TLSA record.
Will this mean that this port is opened for plain text messages too? This would be nothing anyone wants.
Martin.
Hey Martin,
yes, you’re right that connecting to port 25 should use STARTTLS to encrypt the channel. You can configure this on your mail appliance. For example, on a Cisco ESA you can use “TLS required” for that. This still (!) uses port 25, but ONLY accepts messages with STARTTLS.
However, you can also use implicit TLS on port 465 to use encryption by default.
It’s always a bit confusing with those ports. For example, port 587 is *only* used for initial submission from a MUA to the MSA, but NOT between MTAs which is SMTP/message relay. Note that TLSA should be used for message relaying because those MTA parties do not know each other. Hence DANE. ;)
Refer to: https://tools.ietf.org/html/rfc8314
Cheers, Johannes
Unless one is willing to forgo a non-trivial fraction of inbound email, port 25 (the MTA-to-MTA SMTP relay port) needs to continue to accept a mixture of cleartext and TLS encrypted traffic. At Gmail, ~90% of inbound and outbound traffic uses TLS, the other 10% is not all spam:
https://transparencyreport.google.com/safer-email/overview
I feel that in DANE the DNS Server is the replacement of certificate authority to be the trust anchor or the source of trust.
Exactly! Very good summarization! ;)