I was interested to tune my https sites with Apache to support only cipher suites that use the ephemeral Diffie-Hellman key exchange = perfect forward secrecy. But after searching a while through the Internet, only SSLCipherSuite with a few concrete algorithms were presented, while I wanted to use a more generic option such as known from “!MD5”. Here it is:
For a basic understanding, please read those articles: At a Glance – Perfect Forward Secrecy (PFS), Apache documentation SSLCipherSuite Directive, Mozilla Wiki Security/Server Side TLS.
Security (not backward compatibility)
I wanted to use cipher suites with only ephemeral Diffie-Hellman key exchange. (Note that the DH exchange without ephemeral does NOT provide perfect forward secrecy!) Furthermore, I only wanted to use strong ciphers, i.e., AES, and only strong hash algorithms, i.e., not MD5. I was not interested in supporting every old Internet Explorer, and so on. I focused merely on security.
–> This is the Cipher Suite I am using for all my Apache servers:
|
1 |
SSLCipherSuite HIGH:!kRSA:!kDHr:!kDHd:!kSRP:!aNULL:!3DES:!MD5 |
That is:
- All suites under the HIGH classification
- But without the key exchange algorithms of RSA, DH with RSA key, DH with DSA key, and Secure Remote Password (refer to SSLCipherSuite Directive). –> Only ephemeral Diffie-Hellman!
- No NULL authentication
- No 3DES
- No MD5
(Additional, I am always disabling the SSLv3 protocol on all installations:
SSLProtocol all -SSLv3 .)
List of Cipher Suites
OpenSSL can list the selected cipher suites (-v option). Here is my list:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 |
weberjoh@jw-vm11:~$ openssl ciphers -v 'HIGH:!kRSA:!kDHr:!kDHd:!kSRP:!aNULL:!3DES:!MD5' ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384 ECDHE-RSA-AES256-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1 ECDHE-ECDSA-AES256-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1 DHE-DSS-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=DSS Enc=AESGCM(256) Mac=AEAD DHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(256) Mac=AEAD DHE-RSA-AES256-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(256) Mac=SHA256 DHE-DSS-AES256-SHA256 TLSv1.2 Kx=DH Au=DSS Enc=AES(256) Mac=SHA256 DHE-RSA-AES256-SHA SSLv3 Kx=DH Au=RSA Enc=AES(256) Mac=SHA1 DHE-DSS-AES256-SHA SSLv3 Kx=DH Au=DSS Enc=AES(256) Mac=SHA1 DHE-RSA-CAMELLIA256-SHA SSLv3 Kx=DH Au=RSA Enc=Camellia(256) Mac=SHA1 DHE-DSS-CAMELLIA256-SHA SSLv3 Kx=DH Au=DSS Enc=Camellia(256) Mac=SHA1 ECDH-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AESGCM(256) Mac=AEAD ECDH-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AESGCM(256) Mac=AEAD ECDH-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AES(256) Mac=SHA384 ECDH-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AES(256) Mac=SHA384 ECDH-RSA-AES256-SHA SSLv3 Kx=ECDH/RSA Au=ECDH Enc=AES(256) Mac=SHA1 ECDH-ECDSA-AES256-SHA SSLv3 Kx=ECDH/ECDSA Au=ECDH Enc=AES(256) Mac=SHA1 PSK-AES256-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=AES(256) Mac=SHA1 ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256 ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256 ECDHE-RSA-AES128-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1 ECDHE-ECDSA-AES128-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1 DHE-DSS-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=DSS Enc=AESGCM(128) Mac=AEAD DHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(128) Mac=AEAD DHE-RSA-AES128-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(128) Mac=SHA256 DHE-DSS-AES128-SHA256 TLSv1.2 Kx=DH Au=DSS Enc=AES(128) Mac=SHA256 DHE-RSA-AES128-SHA SSLv3 Kx=DH Au=RSA Enc=AES(128) Mac=SHA1 DHE-DSS-AES128-SHA SSLv3 Kx=DH Au=DSS Enc=AES(128) Mac=SHA1 DHE-RSA-CAMELLIA128-SHA SSLv3 Kx=DH Au=RSA Enc=Camellia(128) Mac=SHA1 DHE-DSS-CAMELLIA128-SHA SSLv3 Kx=DH Au=DSS Enc=Camellia(128) Mac=SHA1 ECDH-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AESGCM(128) Mac=AEAD ECDH-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AESGCM(128) Mac=AEAD ECDH-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AES(128) Mac=SHA256 ECDH-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AES(128) Mac=SHA256 ECDH-RSA-AES128-SHA SSLv3 Kx=ECDH/RSA Au=ECDH Enc=AES(128) Mac=SHA1 ECDH-ECDSA-AES128-SHA SSLv3 Kx=ECDH/ECDSA Au=ECDH Enc=AES(128) Mac=SHA1 PSK-AES128-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=AES(128) Mac=SHA1 |
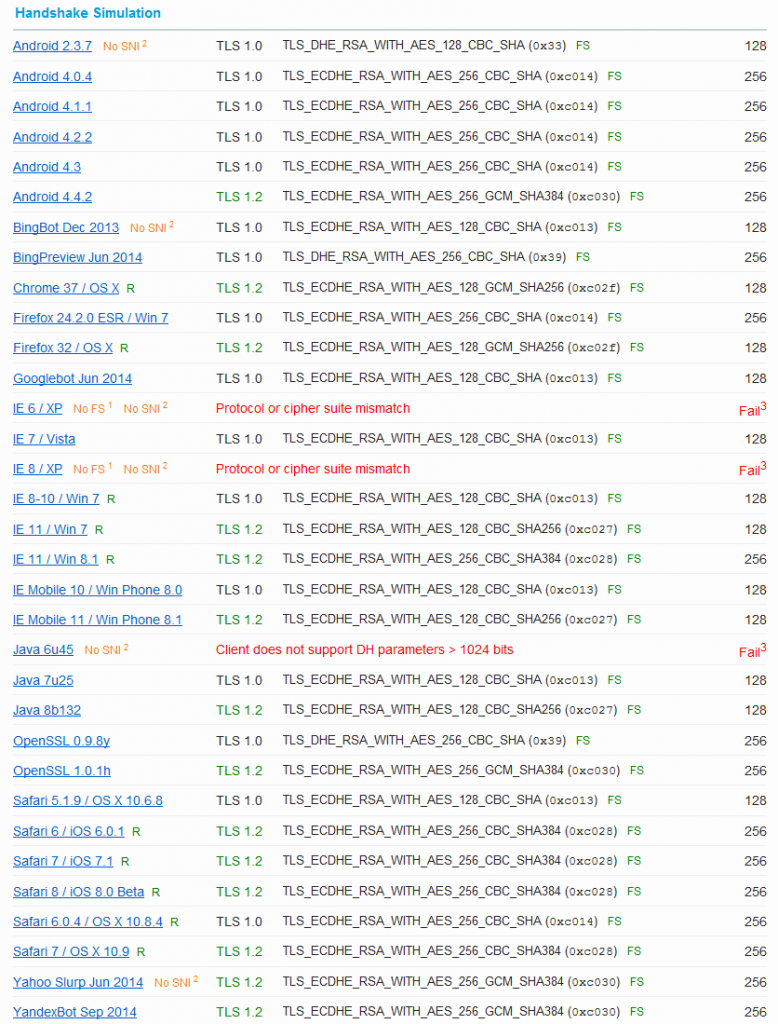
Handshake Simulation
And as always, I am using the SSL Server Test from Qualys SSL Labs at https://www.ssllabs.com/ssltest/. With my presented Cipher Suites, this looks like the following (20. October 2014):
That is: Some old browsers are not supported. But I don’t care since I am not earning money with my servers. I was merely interested in the green “FS” results. ;)
Featured image “One feather” by Thomas Quine is licensed under CC BY 2.0.



Hello!
I’ve used my PA + Apache (SSL) with grade “A” until a few weeks ago.
Today SslLabs report this:
“This server does not support Forward Secrecy with the reference browsers. Grade capped to B. ”
======================
Protocols:
TLS 1.3 No
TLS 1.2 Yes
TLS 1.1 Yes
TLS 1.0 Yes
SSL 3 No
SSL 2 No
Cipher Suites
# TLS 1.2 (server has no preference)
TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) WEAK 112
TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) WEAK 128
TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) WEAK 128
TLS_RSA_WITH_AES_128_GCM_SHA256 (0x9c) WEAK 128
TLS_RSA_WITH_AES_256_CBC_SHA (0x35) WEAK 256
TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d) WEAK 256
TLS_RSA_WITH_AES_256_GCM_SHA384 (0x9d) WEAK 256
# TLS 1.1 (server has no preference)
TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) WEAK 112
TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) WEAK 128
TLS_RSA_WITH_AES_256_CBC_SHA (0x35) WEAK 256
# TLS 1.0 (server has no preference)
TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) WEAK 112
TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) WEAK 128
TLS_RSA_WITH_AES_256_CBC_SHA (0x35) WEAK 256
Protocol Details:
Forward Secrecy No WEAK (more info)
======================
This is the Apche config:
—————
SSLEngine on
SSLOptions +FakeBasicAuth +ExportCertData +StrictRequire
SSLProtocol all -SSLv2 -SSLv3
SSLHonorCipherOrder off
SSLCipherSuite “AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:NULL:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4”
————–
Changing SSLHonorCipherOrder to “on” not solve the problem.
I think it is also necessary to adapt SSLCipherSuite.
Have you a feedback about this with the last PAN-OS 8.x ?
Best regards
Sim
Hey Sim. Sorry, I don’t have an up-to-date list currently. But there are other resources on the web. Google is your friend. ;)
What do you mean about PAN-OS 8.x? You only have very limited settings under Device -> Certificate Management -> SSL/TLS Service Profile. As far as I know you cannot specify the ciphers precisely.
Ciao, Johannes