While preparing for my CCNP SWITCH exam I built a laboratory with 4 switches, 3 routers and 2 workstations in order to test almost all layer 2/3 protocols that are related to network management traffic. And because “PCAP or it didn’t happen” I captured 22 of these protocols to further investigate them with Wireshark. Oh oh, I remember the good old times where I merely used unmanaged layer 2 switches. ;)
In this blogpost I am publishing the captured pcap file with all of these 22 protocols. I am further listing 46 CHALLENGES as an exercise for the reader. Feel free to download the pcap and to test your protocol skills with Wireshark! Use the comment section below for posting your answers.
Of course I am running my lab fully dual-stacked, i.e., with IPv6 and legacy IP. On some switches the SDM template must be changed to be IPv6 capable such as sdm prefer dual-ipv4-and-ipv6 default .
(In two upcoming posts I will first list many show commands from the routers/switches in the lab that are related to the CCNP SWITCH protocols, while in a third one I will show all answers to the proposed questions here with appropriate Wireshark screenshots. And if you are interested in some more pcap files on my site follow the pcap tag. Posts with some Wireshark screenshots and explanations are tagged with Wireshark.)
The pcap file consists of 3893 packets (with 50 % spanning-tree messages). The following zip file is 72 kb in size with this sha256 hash: 4274C8C61BCFB3ADE0557535164AFCEB7FCE47C59601DBFB85059909D5FF8F32.
The challenges are basically related to the protocols but a few can only be answered when using Wireshark and some of its features. If you want to answer all challenges you can use the following “template” for them. In Wireshark you can often use the right-mouse-click with Copy -> Value. Please use the comment section to post your answers! ;)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 |
STP1: STP2: STP3: CDP1: CDP2: VTP1: VTP2: VTP3: DTP: LACP1: LACP2: LLDP: UDLD: HSRP: DHCP1: DHCP2: DHCP3: DHCP4: SNMP: Syslog: NTP: IP SLA: DNS1: DNS2: DNS3: DNS4: TFTP1: TFTP2: TFTP3: TFTP4: ARP: LOOP: RIP: RIPng: ICMPv6 RS/RA1: ICMPv6 RS/RA2: ICMPv6 NS/NA: ICMPv6 Ping: ICMP: SSH: BONUS1: BONUS2: BONUS3: BONUS4: BONUS5: BONUS6: |
Protocols, Protocols, Protocols
Of course I preferred IPv6 rather than legacy IP for all “above layer 2” protocols. Examples are DNS, NTP, SNMP, and SSH. In the following I am only listing the protocols by name and their basic configuration. If you are not familiar with any of these protocols, please wikipedia it yourself. Here we go:
- STP (Spanning Tree Protocol) <- set to spanning-tree mode rapid-pvst , appears per default every 2 seconds on all switch ports per VLAN! I additionally use spanning-tree loopguard default spanning-tree portfast default , and spanning-tree portfast bpduguard default . CHALLENGE: What is the root bridge identifier for VLAN 121? 2nd CHALLENGE: At what time (relative to the beginning of the trace) did the first topology change occur? 3rd CHALLENGE (a bit tricky): What is the port identifier in VLAN 30 from bridge “00:21:1b:ae:31:80”. I mean, what is the ID when it is correctly split into the port prio and the port number? That is, how is the ID displayed on a Cisco device when the “show spanning-tree” command is issued? (Hint: This is the 1998 version of 802.1D, not the 2004.)
- CDP (Cisco Discovery Protocol) <- appears per default every few seconds. CHALLENGE: What is the Cisco IOS Software version running on the CCNP-LAB-S1 switch? 2nd CHALLENGE: What is the native VLAN from the same device?
- VTP (VLAN Trunking Protocol) <- manually added a new VLAN on the VTP server while capturing. CHALLENGE: What is the management domain of VTP? 2nd CHALLENGE: What is the name von VLAN 30? (Hint: The VLAN ID inside the “ISL VLAN ID” field is not in decimal but hexadecimal notation.) 3rd CHALLENGE: What is the last configuration revision?
- DTP (Dynamic Trunking Protocol) <- appears per default. CHALLENGE: What is the “Trunk Operating Status” from the sender ID “00:21:1b:ae:31:99”?
- LACP (Link Aggregation Control Protocol) <- appears on a port that is within a channel-group active|passive. CHALLENGE: What is the “Actor” and “Partner” port as seen from the actor “00:0a:8a:a1:5a:80”? 2nd CHALLENGE: What is the partner system priority?
- LLDP (Link Layer Discovery Protocol) <- after lldp run on global configuration. CHALLENGE: What is the IPv6 management address of CCNP-LAB-S1?
- UDLD (Unidirectional Link Detection; where is the P for Protocol here?!?) <- activated globally with udld aggressive , per default only on fiber ports. CHALLENGE: Which fiber interface port on device “FOC0630Z3KZ” is used?
- HSRP (Hot Standby Routing Protocol) <- Version 2 for IPv6 and legacy IP, both with md5 authentication. CHALLENGE: What is the virtual IPv6 address for HSRP group 127?
- DHCP (Dynamic Host Configuration Protocol) <- since I have configured several VLANs with DHCP server, CHALLENGE: What is the client MAC address that requests an IPv4 address? 2nd CHALLENGE: What is the
hosts vendorhostname of the client? 3rd CHALLENGE: Which IPv4 address did it request? 4th CHALLENGE: What IPv4 address did it actual get? - SNMPv2c (Simple Network Management Protocol aka Security Not My Problem) <- I am using my MRTG/Routers2 for querying the three routers in this lab. Yes, you can read out my SNMP community string in plaintext. ;) CHALLENGE: What is the community string?
- Syslog <- though not covered explicitly in CCNP SWITCH. CHALLENGE: What kind of information was sent by 192.168.121.2?
- NTP (Network Time Protocol) <- periodically, configured with IPv6. CHALLENGE: What type of NTP server is the configured IPv6 server? I mean: Which type of clock does it use?
- IP SLA (Internet Protocol Service Level Agreement) <- ip sla responder on one router, “ip sla … udp-jitter …” on another. UDP Port 1967, it seems that Wireshark has no decoder for this Cisco proprietary protocol, display filter: udp.dstport == 1967 || udp.srcport == 1967 . CHALLENGE: Which two routers (IPv4 address) are the SLA responders?
- DNS (Domain Name System) <- manually when pinging. CHALLENGE: What is the IPv6 address of the DNS server? 2nd CHALLENGE: Which name was queried? 3rd CHALLENGE: How many hops is the DNS server away? 4th CHALLENGE: Is the response DNSSEC validated?
- TFTP (Trivial File Transfer Protocol) <- automatically after every “copy run start” due to my “archive” configuration on the routers. Yes, you can read out my complete router config in the tcpdump trace. ;) Feel free to crack my trivial passwords. (You can also use the tool NetworkMiner to extract the file.) CHALLENGE: What is the password of the user “weberjoh”? 2nd CHALLENGE: What is the “enable secret” password? 3rd & 4th CHALLENGE: What are the passwords in plaintext? Tip: hashcat.
- ARP (Address Resolution Protocol) <- Normal IPv4 networking stuff. CHALLENGE:
“192.168.121.1 is at ???”“192.168.121.2 is at ???” - LOOP (Ethernet Configuration Testing Protocol) <- What is this? Have never heard of it so far. CHALLENGE: How many different MAC addresses sourced a loop frame?
The following protocols are not directly mentioned within the CCNP SWITCH course but they appear in the trace since I used them for some reasons:
- RIPv2 (Routing Information Protocol) <- between my two routers, because it is simple and I am always using OSPF anywhere, so I wanted to test RIP in here. (Refer to this blogpost for OSPFv2 for IPv4.) CHALLENGE: Which two routers (IPv4 source addresses) advertise the default route with a metric of 1?
- RIPng <- same as above. Yes, I know, you are seeing my global unicast prefixes here. But I don’t care – it’s only a lab. And my /48 prefix is easy to find out anyway. ;) I tuned the timers a little bit to have a faster convergence time: timers 10 30 10 20 . (If you are interested in OSPFv3 for IPv6 refer to this blogpost.) CHALLENGE: Which two routers (IPv6 link-local address) advertise the default route?
- ICMPv6 RS/RA (Internet Control Message Protocol) Router Solicitation/Advertisement, icmpv6.type == 133 || icmpv6.type == 134 <- because I have configured at least one VLAN with IPv6. CHALLENGE: Which IPv6 prefixes are advertised? 2nd CHALLENGE: How many router solicitations are directly answered with router advertisements?
- ICMPv6 NS/NA (Internet Control Message Protocol) Neighbor Solicitation/Advertisement, icmpv6.type == 135 || icmpv6.type == 136 <- Normal IPv6 traffic. CHALLENGE: Which global unicast IPv6 address is requested in the duplicate address detection (DAD) process?
- ICMPv6 Ping, icmpv6.type == 128 || icmpv6.type == 129 <- Every 60 seconds from the “IP SLA” configuration. And five pings after a manual ping from the router CLI. CHALLENGE: What is the value of the “Data” field for the ping to “2a01:488:42:1000:50ed:8588:8a:c570”?
- ICMP for legacy IP <- I have no classical pings in my trace but timestamp request/reply packets due to the “icmp-jitter” test within an IP SLA. CHALLENGE: How many request/reply packages are sent during each run of the IP SLA?
- SSH (Secure Shell) via IPv6 to ccnp-lab-r2, fun fact: This is the only tcp.stream within the whole trace. ;) CHALLENGE: What is the client protocol version in the SSH session?

BONUS CHALLENGE: There is still one protocol left in the trace. Which one?
2nd BONUS CHALLENGE: Furthermore, there are some UDP connections from/with high ports on both sides. What are these connections related to?
3rd BONUS CHALLENGE: How many conversations over IPv6/IPv4/TCP/UDP are in the trace?
4th BONUS CHALLENGE: What is the average “packets per second” through this trace file?
5th BONUS CHALLENGE: How many IPv6/IPv4 packets are in the trace?
6th BONUS CHALLENGE: What is the MAC address of 192.168.121.1?
But still not all
I am sorry, but the following protocols/technologies are NOT inside in this pcap trace though they are covered in the SWITCH course:
- PAgP (Port Aggregation Protocol, Cisco proprietary) <- since I am using LACP.
- MST (Multiple Spanning Tree Protocol) <- since I am using PVST+.
- RADIUS (Remote Authentication Dial-In User Service)
- TACACS+ (Terminal Access Controller Access-Control System Plus)
- EAPOL (Extensible Authentication Protocol over LAN)
- SNTP (Simple Network Time Protocol) <- but NTP.
- SNMPv3 <- sorry about that. Lack of time. I used SNMPv2c.
- VRRP (Virtual Router Redundancy Protocol) <- because I have HSRP already.
- GLBP (Gateway Load Balancing Protocol) <- dito, you can’t have everything. ;)
What I have missed (it’s too late to do the trace for the hundredth time):
- Telnet <- should not be used anyway
- ICMP for legacy IP with ping (simple echo-request)
- Traceroute <- that is, decreasing TTLs
- NetFlow <- would have been easy, but I forgot it
- GRE (Generic Routing Encapsulation) <- dito
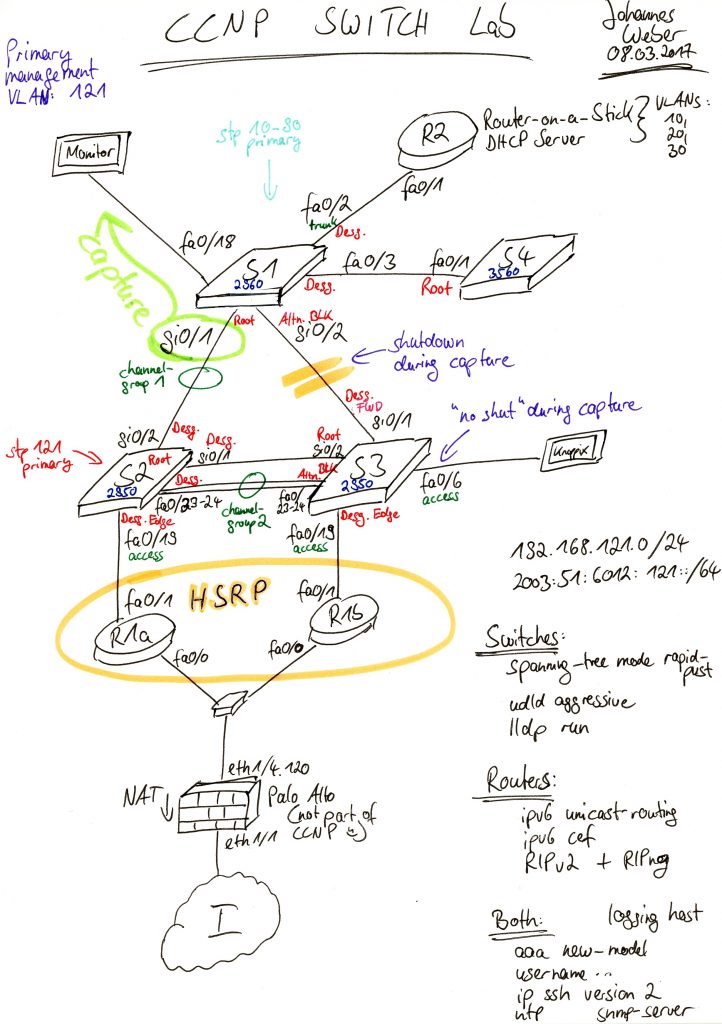
My Lab
Though not really interesting in respect of the protocols, this is the CCNP SWITCH lab I used to create the pcap trace. Note the green “capture” arrow which shows on which interface (gi0/1 on S1) I took it:
It consits of the following components:
- 1x Cisco Catalyst 2960, (C2960-LANBASEK9-M), Version 15.0(2)SE9
- 2x Cisco Catalyst 2950, (C2950-I6K2L2Q4-M), Version 12.1(22)EA14
- 1x Cisco Catalyst 3560, (C3560-IPSERVICESK9-M), Version 12.2(55)SE10
- 3x Cisco Router 2811, (C2800NM-ADVENTERPRISEK9-M), Version 15.1(4)M9
- 2x old Notebooks, Dell or somewhat, running either Ubuntu or Knoppix Linux
I am using switchport trunk native vlan 2 for my default not-vlan-1 trunk native vlan and switchport access vlan 3 for my default not-vlan-1 access vlan. (This is sometimes irritating in the trace since some management protocols such as LACP, VTP, and CDP are still using vlan 1 while some other management protocols such as UDLD and DTP are using the configured native vlan 2.)
I captured on switch S1 with the following commands:
|
1 2 |
monitor session 1 source interface Gi0/1 monitor session 1 destination interface Fa0/18 encapsulation replicate |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
CCNP-LAB-S1#show monitor detail Session 1 --------- Type : Local Session Description : - Source Ports : RX Only : None TX Only : None Both : Gi0/1 Source VLANs : RX Only : None TX Only : None Both : None Source RSPAN VLAN : None Destination Ports : Fa0/18 Encapsulation : Replicate Ingress : Disabled Filter VLANs : None Dest RSPAN VLAN : None |
I am still a bit confused about the “encapsulation replicate”. Without it no layer 2 traffic was monitored. However, now I have the problem that many but not all packets in the pcap file have the 802.1Q vlan tag. This irritates when scrolling through the packets.
I used the following sequence during the 5 minute trace:
- Topology change: shutdown of gi0/2 on switch S1.
- Creation of a new VLAN on VTP server switch S1.
- Reboot of router R1b for HSRP and routing changes.
- shutdown and no shut of access port eth0/6 on switch S2 with Knoppix Linux machine for DHCP/ICMPv6.
- SSH to router R2 for at least one tcp.stream. ;)
- copy run start on router R2 to trigger TFTP copy.
- clear hosts and ping ip.webernetz.net from router R2 for DNS and ICMPv6.
- Another topology change: no shut of gi0/2 on switch S1.
Have fun. ;) And happy easter. The Lord is risen indeed!
Featured image: “Data Center” by Bob Mical is licensed under CC BY-NC 2.0.



Fun lab, I used to have one like this for my old ccnp/dp days.
For the low hanging fruit you can use basic protocol display filters to narrow down the amount of packets to answer the questions.
Your snmp one is — n5rAD1ig314IqfioYBWw
Fun test as a refresher too.. Nice work…
Question Name Result
1 STP1: 00:0a:8a:a1:5a:80
2 STP2: 4.762981
3 STP3: 72
4 CDP1: 15.0(2)SE9
5 CDP2: 2
6 VTP1: webernetz.net
7 VTP2: VLAN30nochnvlan
8 VTP3: 13
9 DTP: Trunk/On (0x81)
10 LACP1: 26 and 282
11 LACP2: 32768
12 LLDP: 2003:51:6012:121::10
13 UDLD: Gi0/2
14 HSRP: fe80::5:73ff:fea0:7f (0x7f == 127)
15 DHCP1: 00:21:70:e9:bb:47
16 DHCP2: Dell
17 DHCP3: 192.168.20.11
18 DHCP4: 192.168.30.11
19 SNMP: n5rAD1ig314IqfioYBWw
20 Syslog: ACL permit on the vty-access
21 NTP: Stratum-2
22 IP SLA: 192.168.121.253 and 192.168.121.254
23 DNS1: 2003:51:6012:120::a08:53
24 DNS2: ip.webernetz.net
25 DNS3: 2
26 DNS4: No
27 TFTP1: $1$kI2F$Sz18KSQV/D/QJpbpIGpH10
28 TFTP2: $1$Z.9j$Nvobsx9NvJzqtRLQqR.9b0
29 TFTP3: asdfasdf
30 TFTP4: password
31 ARP: 00:00:0c:9f:f0:79
32 LOOP: 3
33 RIP: 192.168.121.253 and 192.168.121.254
34 RIPng: fe80::21a:6cff:fea1:2b99 and fe80::21e:7aff:fe79:3f11
35 ICMPv6 RS/RA1: 2003:51:6012:121::/64 and 2003:51:6012:122::/64
36 ICMPv6 RS/RA2: None
37 ICMPv6 NS/NA: 2003:51:6012:121::2
38 ICMPv6 Ping: 0102030405060708090a0b0c0d0e0f101112131415161718191a1b1c
39 ICMP: 10 requests, 10 replies
40 SSH: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.1
41 BONUS1: DEC DNA remote console (0x6002)
42 BONUS2: There is a rate limiter on 1967 to prevent DoS. To not have the rate limiter interfere with the IP SLA, the responder dynamically moves the request/reply traffic to a high udp port.
43 BONUS3: IPv4: 22, IPv6: 27, tcp: 1, udp: 56
44 BONUS4: 11,6272126
45 BONUS5: 1349
Hey dvh, congrats for being the first who has answered all challenges! ;)
You got 38 points since the following 7 challenges are not correct: STP1, STP3, NTP, LOOP, RIPng, ICMPv6, BONUS2.
Anyway, thanks for posting your answers!
STP1: 24576 / 121 / 00:0a:8a:a1:5a:80
STP2: 4.762981000; Frame 42
STP3: 128.72 So the Port Neighbor is Port 72
CDP1: Cisco IOS Software, C2960 Software (C2960-LANBASEK9-M), Version 15.0(2)SE9, RELEASE SOFTWARE (fc1)
CDP2: VLAN 2
VTP1: webernetz.net
VTP2: VLAN30nochnvlan
VTP3: 13
DTP: Trunk
LACP1: Actor= 26, Partner = 282
LACP2: 32768
LLDP: 2003:51:6012:121::10
UDLD: Gi0/2
HSRP: fe80::5:73ff:fea0:7f
DHCP1: 00:21:70:e9:bb:47
DHCP2: Dell
DHCP3: 0.0.0.0 -> None preferred
DHCP4: 192.168.30.11
SNMP: n5rAD1ig314IqfioYBWw
Syslog: INFO – %IPV6_ACL-6-ACCESSLOGP: -> 2 Entrys
NTP: 44:43:46:61 ‘DCFa’ -> DCF77 with amplitude modulation
IP SLA: 192.168.121.254, 192.168.121.253
DNS1:2003:51:6012:120::a08:53
DNS2:ip.webernetz.net
DNS3:2
DNS4: No
TFTP1:$1$kI2F$Sz18KSQV/D/QJpbpIGpH10
TFTP2:$1$Z.9j$Nvobsx9NvJzqtRLQqR.9b0
TFTP3:asdfasdf
TFTP4:password
ARP: ARP for 192.168.121.1 Is not inside the trace(Is 00:14:69:9e:11:41). But 192.168.121.2 is at 00:1e:7a:79:3f:11
LOOP:5
RIP:192.168.121.254, 192.168.121.253
RIPng:fe80::21a:6cff:fea1:2b99, fe80::214:69ff:fe9e:1141
ICMPv6 RS/RA1: 2003:51:6012:121::
ICMPv6 RS/RA2: none
ICMPv6 NS/NA: 2003:51:6012:121::cafe
ICMPv6 Ping: 01:02:03:04:05:06:07:08:09:0a:0b:0c:0d:0e:0f:10:11:12:13:14:15:16:17:18:19:1a:1b:1c
ICMP: 1 Request and 1 Response to each Device .253 and .254 per turn
SSH: SSHv2
BONUS1: DEC DNA Remote Console (0x6002))
BONUS2:IP SLA
BONUS3: IPv4=22 IPv6=27 UDP=56 TCP=1
BONUS4: 11.6
BONUS5: 1349
After rereading the questions I have to precise some answers:
DHCP3: 192.168.30.11
ICMP: 10 Requests and 10 Responses to each Device .253 and .254 per turn
SSH: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.1 Protocol: SSHv2 ClientSW: openssh 7.2p2 for Ubuntu
ICMPv6 RS/RA1: 2003:51:6012:121::/64 , 2003:51:6012:122::/64
BONUS2: IP SLA Jitter test
BONUS5: IPv4= 586, IPv6=763
DHCP3: First Request: 192.168.20.11 answered with NAK
Second Request 192.168.30.11 after a DISCOVER and an OFFER
Hey Christian,
wow, finally thats 100 %! Nice work!
PS: Shit, I wrote the wrong IPv4 address for the ARP question. Thanks for mention it. I corrected it.
STP1: 00:0a:8a:a1:5a:80
STP2: 4.762981000
STP3: 128.72
CDP1: Version 15.0(2)SE9
CDP2: 2
VTP1: webernetz.net
VTP2: VLAN30nochnvlan
VTP3: 13
DTP: 0x00000001 (Trunk)
LACP1: 26 (actor), 282 (partner)
LACP2: 32768
LLDP: 2003:51:6012:121::10
UDLD: Gi0/2
HSRP: fe80::5:73ff:fea0:7f
DHCP1: 00:21:70:e9:bb:47
DHCP2: Dell
DHCP3: 192.168.30.11
DHCP4: 192.168.30.11
SNMP: n5rAD1ig314IqfioYBWw
Syslog: Informational, IPv6 Access Log
NTP: DCF (?) tricky question
IP SLA: 192.168.121.253, 192.168.121.254
DNS1: 2003:51:6012:120::a08:53
DNS2: ip.webernetz.net
DNS3: 2
DNS4: No
TFTP1: $1$kI2F$Sz18KSQV/D/QJpbpIGpH10 (hash)
TFTP2: $1$Z.9j$Nvobsx9NvJzqtRLQqR.9b0 (hash)
TFTP3: asdfasdf
TFTP4: password
ARP: 00:00:0c:9f:f0:79 (wow, cool one!)
LOOP: 5
RIP: 192.168.121.253, 192.168.121.254
RIPng: fe80::21a:6cff:fea1:2b99, fe80::214:69ff:fe9e:1141
ICMPv6 RS/RA1: 2003:51:6012:122::/64, 2003:51:6012:121::/64
ICMPv6 RS/RA2: 0
ICMPv6 NS/NA: 2003:51:6012:121::cafe
ICMPv6 Ping:01:02:03:04:05:06:07:08:09:0a:0b:0c:0d:0e:0f:10:11:12:13:14:15:16:17:18:19:1a:1b:1c
ICMP: 10
SSH: 2.0 (Openssh 7.2 lib)
BONUS1: DECNet MOP (I’d almost given up for that question)
BONUS2: IP SLA UDP Jitter with custom ports (from config file)
BONUS3: IPv6 – 27 / IPv4 – 22 / TCP – 1 / UDP – 56
BONUS4: 11.6
BONUS5: 763/586
DHCP3: I missed NAK, so the first try indeed was 192.168.20.11
STP3: Interesting question. You’ve said that this is 802.1D-1998, but I see in Wireshark “Protocol Version Identifier: Rapid Spanning Tree (2), BPDU Type: Rapid/Multiple Spanning Tree (0x02)”. Is it correct?
Also I’ve read that Port ID between STP-1998 and -2004 versions has been changed a bit (prio.nbr was 8+8 bit and became 4+12 bit) but here (if I understand correctly) both variants are decoding the same way. Interesting to see your answers!
Hey Vladimir,
wow, that’s 44 out of 45 questions correct. Only the STP1 question is not complete (though I can see that you got the correct packet…).
Concerning ARP: Sorry, I misspelled the question. It sould read “192.168.121.2 is at ???”. What did you answer? Would be nice to see since I don’t find 192.168.121.1 in the trace at all. ;)
Concerning NTP: Yes, correct, its a DCF-77 receiver. Seen in the Reference ID.
Concerning STP: Your answer with 128.72 is correct. If the split of 0x8048 would be 4+12 bits then it would result in 8.72 and not 128.72. I used “spanning-tree mode rapid-pvst” on all Cisco switches.
Hi Johannes,
192.168.121.1 actually IS in the trace. But it’s not in ARP packet, of course. And it’s not easy to find therefore.
If you open IPv4 HSRP packet from 192.168.121.254 router (no.40 for example), you’ll see that ‘vitrual IP address’ field contains IP of 192.168.121.1 and this group has 00:00:0c:9f:f0:79 MAC address. So, despite we don’t see any conversation/ARP packet with this IP, I assume in case of such request we would see ‘192.168.121.1 is at 00:00:0c:9f:f0:79’
Haha, great, you’re absolutely correct. ;) Would have been a great bonus challenge!
Hallo Johannes,
First of all I would like to say that this is a great idea and I really enjoyed going through the challenges.
One of the things I’m missing is the cracking of the Cisco IOS secret passwords… As far as I’m aware this does not work and they’re still considered safe. Yet I see in the comments section that the colleagues have done it. Have I missed something?
Hey boyan,
thanks for your comment.
You must distinguish between secure and brute-force. You are correct, that you can NOT reverse the hashes. However, you can do a brute-force attack by simply trying everything until you have the same hash as the ones I published.
Since my passwords are that simple you must not even do a real brute-force attack of but only a dictionary attack. This might be successful after a few seconds. ;)
(If I had used real passwords with 12+ chars generated randomly, you would never succeed…!)