This is a cool and easy to use (security) feature from Palo Alto Networks firewalls: The External Dynamic Lists which can be used with some (free) 3rd party IP lists to block malicious incoming IP connections. In my case, I am using at least one free IP list to deny any connection from these sources coming into my network/DMZ. I am showing the configuration of such lists on the Palo Alto as well as some stats about it.
Lists
What is an external dynamic list? It is a list of known malicious sources maintained by some providers/persons on the Internet. These IP lists can be used to blacklist/block/deny connections from those sources. A good overview of such lists is “Blocklists of Suspected Malicious IPs and URLs” from Lenny Zeltser. I am currently using the following well-known lists: “All Cybercrime IP Feeds” by FireHOL: http://iplists.firehol.org/.
This list is a combination of other sources that also include fullbogons and other entries. FireHOL shows many graphs and stats about the distribution from their listed IP addresses. Follow the link above and have a look!
What about IPv6? Well, it seems that only legacy IP is widely supported. Bad. FireHOL does not list any statement about that. I am not happy with this, but I also know that it is not easy to maintain IPv6 lists due to the large address space. (Should an IPv6 blacklist block a /128, /64 or even a /48 in case of abuse?) At least the Spamhaus Project has an IPv6 list, called DROPv6.
Some further notes:
- You should always check the quality of the list before using it. To my mind this mentioned list is quite “good”, however, note that it could be abused, too. Do some research about its trustworthiness before using it in your policies.
- The list is only an IP address list, that is, it is useful for blocking incoming connections. For outgoing (user-initiated) connections, you can use URL lists rather than IP lists. Lenny mentioned a few of them in his blog post. And the Palo Alto firewall is also able to use domain and even URL lists for security policies, etc.
Usage within Palo Alto
I am currently using a PA-200 with PAN-OS 7.1.7. (Official documentation here.) The blacklists are configured under Objects -> External Dynamic Lists. They are from type “IP List”. Those dynamic objects can then be used within a security policy. In my case, I have added two deny policies at the very beginning of my whole ruleset. Immediately after committing the traffic log shows denied connection from various IPv4 addresses:
Some Stats
At first, I was interested in whether the whole blacklists are used correctly by the firewall. There are some CLI commands to see/refresh the lists such as:
|
1 2 3 4 |
weberjoh@pa> request system external-list ? > refresh refresh external-lists > show Print IPs/Domains/URLs in an external list > url-test test accessibility for url |
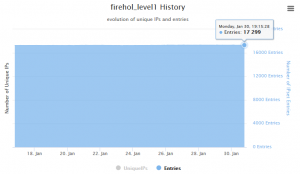 I captured this screenshot from the FireHOL page that shows 17.299 entries on January 30th, 2017. In fact, exactly the same valid entries were listed in the Palo Alto dynamic list at the same time, as the following listing shows. (Note that there are not only /32 host IPv4 addresses but also bigger [bigly?] networks such as /20):
I captured this screenshot from the FireHOL page that shows 17.299 entries on January 30th, 2017. In fact, exactly the same valid entries were listed in the Palo Alto dynamic list at the same time, as the following listing shows. (Note that there are not only /32 host IPv4 addresses but also bigger [bigly?] networks such as /20):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
weberjoh@pa> request system external-list show type ip name dyn_firehol vsys1/dyn_firehol: Next update at : Mon Jan 30 21:00:21 2017 Source : https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level1.netset Referenced : Yes Valid : Yes Total valid entries : 17299 Total invalid entries : 34 Valid ips: 0.0.0.0/8 1.10.16.0/20 1.32.128.0/18 1.93.0.224 1.116.0.0/14 1.178.179.217 1.179.170.7 [...] |
Of course, it looks quite the same with IPv6, here with the Spamhaus DROPv6 list:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
weberjoh@pa> request system external-list show type ip name dyn_Spamhaus-DROPv6 vsys1/dyn_Spamhaus-DROPv6: Next update at : Wed Feb 15 05:13:38 2017 Source : https://www.spamhaus.org/drop/dropv6.txt Referenced : Yes Valid : Yes Total valid entries : 19 Total invalid entries : 4 Valid ips: 2a07:5807::/32 2a06:2a00::/29 2a06:e480::/29 2a06:4740::/29 2a06:df80::/29 2402:6680::/32 2a0a:c00::/29 2a06:f680::/29 2404:e180::/32 2a07:5780::/29 2a06:d240::/29 2a00:dfe0::/29 2a07:5786::/32 2607:f2d0::/32 2803:5380:ffff::/48 |
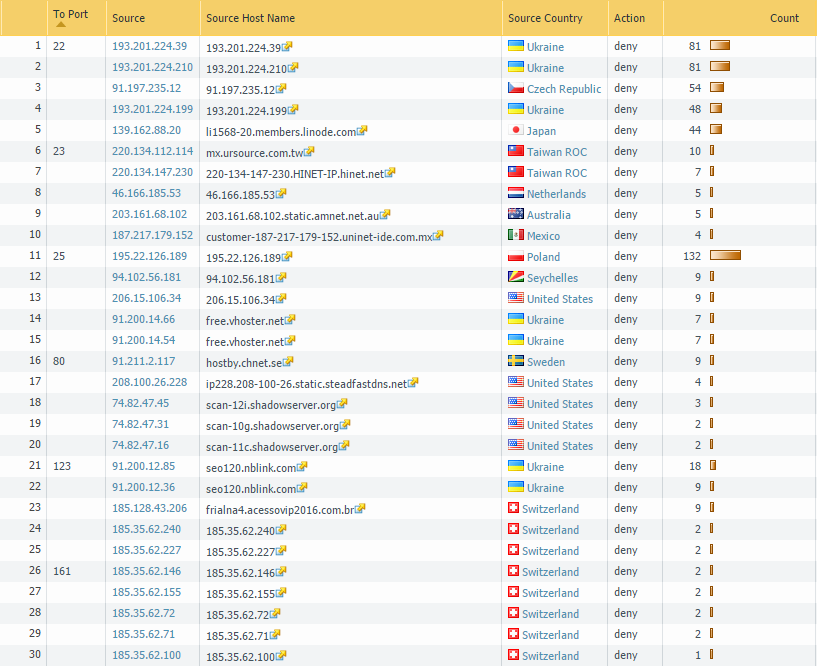
Now here is a custom report that shows all denied connections during the last calendar week, sorted by count (top 5), grouped by port. Many well-known ports such as SSH, telnet, SMTP, HTTP, NTP, SNMP, etc. are scanned from different IPv4 addresses all over the world:
I really like this feature, at least for my lab where not everything is business-critical. To my mind blocking some “false positives” is still better than allowing some malicious connections (false negatives).
Featured image: “Lists” by Steven Lilley is licensed under CC BY-SA 2.0.


I use mainly this EDLs:
– Team Cymru’s BOGON (catching mostly ping and bittorrent traffic from malconfigured 100.64.0.0/10)
– Spamhaus DROP (lots of abusive traffic, port scans)
– Spamhaus EDROP (minimal traffic)
– DSHIELD top 20 (10x traffic from DROP list, scans, shodan.io, “scan the internet” university projects)
– Team Cymru’s FULLBOGON (not a lot of traffic)
Hi, Thanks for the great stuff. I have a query,
From Info Sec Team , we’re getting an URL(http://example.com) to be blocked in firewall. Can we accomplish this by blocking in URL filtering profile or by any other way.
Could you please assist.
Create a custom URL list with the domain, allow it in filter, and include it in the policy as allowed traffic.
Ciao, first of all thanks for thsi marvellous article. Only one question: when i add the link of firehol list to the firewall and click on TEST SOURCE i obtain URL ACCESS ERROR. Please can you help me?
Thanks indeed
Ciao,
Marco
Hi marco,
I am not quite sure what might be your problem. You are talking about this URL: “https://raw.githubusercontent.com/firehol/blocklist-ipsets/master/firehol_level1.netset”? I can access it from my computer, hence it’s working in general.
Maybe you cannot access it from your firewall because you’re running in a blocking ACL somewhere else?
It is likely the https giving you problems. Try using http: for the link and see if they serve it without SSL. I had a bunch of lists that didn’t work using https: even though they didn’t use login credentials, but were fine when switched to http (spamhaus drop, edrop, etc.). I suspect the FW is not trusting the CAs used in the https cert.
There is a new feature in regards to EDL which is really cool.
Palo Alto is now offering “EDL Hosting Service” for free where you can get MS Azure and M365 IPs and URLs in EDL format.
Up until now you had to run a Minemeld server on your own to parse the IP and URL feed provided by MS into EDL format.
With this new service it is now possible to just consume these lists in the right format (and updated frequently) directly from PAN servers:
https://docs.paloaltonetworks.com/resources/edl-hosting-service.html